Security Management – Englewood Health Care
Organization overview
Englewood Health Care is a healthcare facility that services a broad metropolitan area region. The organization comprises several units that provide a wide range of medical services, including urgent care, diagnostic services, primary care, surgery, and rehabilitation programs. The facility is medium-sized, with 500 employees who include physicians, registered nurses, administrative personnel, security personnel, IT specialists, and other support staff.
Key Information
- Organization Type: Healthcare facility (hospital, outpatient services)
- Englewood, New Jersey, with multiple satellite locations
- Sector: Health services (medical, emergency, outpatient, rehabilitation)
- Services Provided: Primary care; urgent care; specialist consultation; diagnostic services; surgeries; rehabilitation; and wellness programs.
- Relevant Security Issues: Protection of patient data (HIPAA), physical security of the facilities, cybersecurity of medical records, and compliance with industry regulations.
Chart
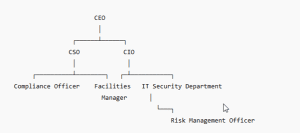
. Security Working Group (WG) Structure and Ties
The Security Working Group (WG) is a component of the organizational hierarchy, comprising representatives from various departments. The working group is fundamental to the organization’s security, with the Chief Security Officer (CSO) as the primary point of contact. The members of the WG work on various projects related to security, both physical and digital, as well as compliance, risk management, and other multidisciplinary fields.
Members of the WG
- CSO (Lead of WG) – Directs security operations and drives interdepartmental collaboration on security activities.
- CIO – Collaborates with other departments to develop and implement cybersecurity strategies.
- Compliance Officer – Monitors organizational compliances to set regulations and patterns of the industry.
- Facilities Security Manager – Deals with implementation of security policies in the healthcare facilities (Force & Initiative, 2013).
- Risk Management Officer – Evaluates security risks in cybersecurity, physical security, and other associated compliance concerns.
This group integrates security to make certain that all healthcare organization’s operations and activities are secured and safe.
Memo: Information Exchange between Security Working Group (WG) and Other Units
To: CEO, CSO, IT, Facilities, Legal and Compliance
From: CSO Englewood Health Care
Subject: Information Exchange on Security Management
Date:
For security issues pertaining to risk management of Englewood Health Care, there are information flow gaps as far as communication is concerned. Below is the communication flow that has to be followed.
Incident Reporting
All possible security and compliance risk issues will be escalated to the CSO by the other department heads, such as IT, Facilities, and Risk Management. If such an incident occurs, the CSO will, in turn, report it to the CEO.
Security Updates
The CSO will hold Regular Meetings with the Security Working Group which consists of IT, Legal, Facilities, and Risk Management representatives. Ongoing security issues, and assessment of risks and compliance challenges will be discussed.
Cross-Departmental Collaboration
The CIO will coordinate with the Facilities Security Manager to integrate procedures for both physical and electronic security. Additionally, any compliance matters, such as HIPAA, will be addressed directly by the Compliance Officer and the Chief Security Officer (CSO).
Escalation Process
For security breaches or gaps that are regulatory, the CSO has the authority to bring these matters directly to the CEO’s attention for quick resolution. This way, the executive branches have full knowledge of very critical security or compliance issues.
Policy Updates and Risk Mitigation
New policies regarding security, risk mitigation, and organizational compliance will be communicated by the Chief Security Officer (CSO) to the whole organization. Each department will ensure that the lower-level units or sub-units within those units receive this information through their department heads (Walsh, 2023).
Week 2: Security Business Requirements
TBD
TBD
Week 4: System Design Principles
TBD
TBD
References
Force, J. T., & Initiative, T. (2013). Security and privacy controls for federal information systems and organizations. NIST Special Publication, 800(53), 8-13. http://dx.doi.org/10.6028/NIST.SP.800-53r4
Walsh, A. P., Hamill, S., & Morrison, I. (2023). Health Information Technology. In Jonas and Kovner’s Health Care Delivery in the United States (13th ed., p. 359). Springer Publishing Company.
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question
Description
Throughout this course, you will be working on several aspects of security management that will result in a Comprehensive Security Management Plan for an organization of your choosing. This plan will allow you to assess the security concerns of your organization and propose needs and changes. The Comprehensive Security Management Plan will introduce methodologies that can be applied to enterprise security design. Each week, you will complete a part of the Comprehensive Security Management Plan, and the final draft will be due at the end of the course. This is the course Key Assignment that you will make contributions to each week.
Assignment (2) Pages

Security Management – Englewood Health Care
The first task in this process will be to select an organization or identify a hypothetical organization to use as the basis of the projects. Next, you will create the shell document for the final project deliverable that will be worked on during each unit. While you proceed through each project phase, content will be added for each section of the document to gradually complete the final project. Appropriate research should be conducted to support the development of the document, and assumptions may be made.
For the first phase of the Comprehensive Security Management Plan document, you will create an enterprise organizational chart in the first document section. A proposed security working group (WG) organization and its ties to the enterprise will be added. Finally, include a 1-page discussion of the flow of information, decision-making communication, and responsibilities of the chief security officer (CSO). Create the skeleton for the Comprehensive Security Management Plan as follows:
• Use Word
• Title Page
o Course number and name
o Project name
o Your name
o Date
• Table of Contents (TOC)
o Use an auto-generated TOC.
o This must be on a separate page.
o This must be 2 levels deep.
o Be sure to update the fields of the TOC before submitting your project.
• Section Headings (Create each heading on a new page with “TBD” as content, except for the sections that are listed under “New Content.”)
o Project Outline (Week 1)
o Security Requirements (Week 1)
o Security Business Requirements (Week 2)
o Security Policy (Week 3)
o System Design Principles (Week 4)
o The Training Module (Week 5)
• References
The following are the project deliverables for Week 1:
• New Content
o Project Outline and Security Requirements
Include a brief description of the real or hypothetical organization in which the Comprehensive Security Management Plan will be implemented.
Include the company’s size, location(s), and other pertinent information.
o Initial Security Projects
Corporate organizational chart
WG structure and ties added to corporate organizational chart
Memo discussing communication flows with WG
• Name the document “yourname_CS654_IP1.doc.”