Security Systems Risk Management
The risk management process plays an essential role in organizations. Organizations and individuals succeed because they take risks in ventures of interest. Huge revenues for most organizations result from investments associated with high risks. Risks should not be avoided in business ventures but controlled through risk control techniques such as reducing the frequency of loss and contractual transfer of responsibility for loss occurrence (Pasha, 2018). Organizations and individuals need to understand the risk management process to reduce possible risks.
Definition of Risk Management and Information Security
A problem that causes losses and threats to an organization’s systems is known as a risk. Risk management entails the process of identifying, assessing, analyzing, and controlling the problems to an organization’s objectives. Most of the problems result from natural calamities, poor management decisions, financial constraints, accidents, changes in technology, and undefined business models. For instance, risks can arise from network failure and unauthorized internet connections in computer-related fields. Creating high-quality software systems cannot solve the problem of network failure and malicious internet users. The management team has to assess and monitor the risks before they escalate (Pasha, 2018). A suitable risk management program enables organizations/ individuals to understand the range of all risks they encounter.
Information security does not only entail preventing unauthorized persons from accessing information. Information is considered secure when it is protected from unauthorized users, disruption, modification, destruction, and recording. Information security covers various fields, ranging from individual data to mobile phones, computers, cybercrimes, and social media platforms. For instance, some strategies secure an organization’s assets, like computers, networks, and data, from unauthorized access. Information security in an organization can be improved by encrypting the company’s devices like computers, establishing solid passwords, updating the organization’s programs regularly, and backing up data regularly. Information is essential in any organization, and therefore, there is a need to manage the risks associated with losing it.
How Information Security Differs From Information Risk Management
Information risk management looks at the threats, vulnerabilities, and impacts on the organization’s goals in case of cybercrime or breach of an organization’s information. Information security looks at preventing information from being accessed by unauthorized users. Information security is enhanced with passwords on computers, regularly updating the organization’s programs and data backups. Confidentiality and integrity are critical virtues for information security. Information risk management is a section of more extensive risk management where risks associated with information security are assessed and monitored.
Security Policies and Their Impact on Risk Management
Information security policies play a vital role in the success of an organization. Security policies define information responsibilities for each employee in an organization. Standard security policies include password creation and management policy, network security policy, data retention policy, access authorization, modification policy, incident response policy, and remote access policy (Mamonov, 2018).
Password Creation and Management Policy
The policy provides guiding mechanisms for creating, changing and safeguarding solid and unique passwords. Only authorized persons, not all employees, should possess passwords to avoid a company information breach. Strong and unique passwords should be used to verify user identities that are authorized to access the organization’s systems or information (Mamonov, 2018). Organizations should consider changing passwords regularly for information security purposes. Only employees of an organization should know the passwords to reduce the risk of non-members accessing information, enhancing information security.
Network Security Policy
Network security policy ensures integrity, confidentiality, and accessibility of information. The policy ensures that routers, switches, and soft wares are appropriate. Failed login attempts are detected under the network security policy. Shutdown and startup of the company’s systems are addressed by the network security policy (Mamonov, 2018). Network security policies play a vital role in risk management. For instance, failed login attempts send a good signal to IT managers to change the passwords to prevent unknown users from accessing the company’s information.
Data Retention Policy
Data retention policy states how to store and destroy data. The policy enables an organization to destroy duplicated data, creating space for the storage of useful information for future use. Useful information should be stored in the form of email for future reference (Mamonov, 2018). This policy is essential in risk management as it ensures the security of sensitive information for future use in decision-making. The policy addresses the risk of data loss.
Access Authorization and Modification Policy
Under this policy, the organization’s systems should only give users access to information required to perform their duties. Sensitive information should be accessed by top management (Eddolls, 2016). HR and IT should be the ones to access passwords to sensitive information within an organization. IT experts should modify the passwords and share them with HR. Access authorization and modification policy reduces the risk of accessing the organization’s sensitive information to junior employees.
Incident Response Policy
The policy is part of the business plan. It is a response to information security response. The policy identifies the incident, eradicates the emergency, and recovers information. After recovery of information, a post-incident is put in place to prevent any other risk associated with disrupting the organization’s systems. Implementation of a post-incident is part of risk management as it prevents the occurrence of a problem for a second time.
Other important security policies include HR policies, SPAM protection policies, system maintenance policies, encryption, and decryption policies. The above-discussed policies play a vital role in risk management. For example, access authorization and modification policies reduce the risk of accessing the organization’s sensitive information to junior employees. Generally, security policies prevent unauthorized individuals from accessing the organization’s information and reduce the risk of losing sensitive information.
Responsibilities of IT and Non-IT Leaders in Risk Management
IT leaders are responsible for developing software and programs for running organizations. They also update the software regularly to reduce the risk of system failure. IT leaders are also in charge of maintaining the organization’s website and protecting it from attacks by creating passwords. Through this, leaders reduce the risk associated with non-members accessing the organization’s information.
Non-IT leaders such as HR are responsible for hiring employees with the required knowledge and skills. Hiring a productive workforce reduces the risks associated with poor performance. Sales leaders are responsible for studying and analyzing the market. A well-analyzed market reduces the risks associated with underproduction and overproduction.
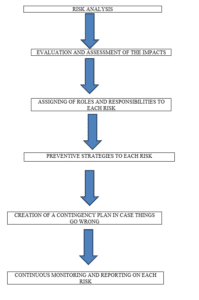
How Risk Management Plans are Tailored to Produce Information and System-Specific Plans
A good risk management plan should meet a specified system plan. For instance, a security risk management plan has to take the following steps.
Risk analysis entails the identification of the risks, documentation, and prioritization. Step 2 entails the evaluation and assessment of the impact of each risk. Step 3 focuses on the responsibilities of each risk. Step 4 requires one to come up with strategies to prevent the risks. Step 5 requires a remedy to step four just in case things did not work in the previous stage. Step 6 requires continuous monitoring and reporting on the risks (Mackay, 2020).
References
Eddolls, M. (2016). Making cybercrime prevention the highest priority. Network Security, 2016(8), 5-8.
Mackay, J. (2020). Steps to writing a management plan
Mamonov, S., & Benbunan-Fich, R. (2018). The impact of information security threat awareness on privacy-protective behaviors. Computers in Human Behavior, 83, 32-44.
Pasha, M., Qaiser, G., & Pasha, U. (2018). A critical analysis of software risk management techniques in large-scale systems. IEEE Access, 6, 12412-12424.
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question
It is an accepted truth that without risk, there can be no gain. Every individual and organization must take some risks to succeed. Risk management is not about avoiding risks but about taking risks in a controlled environment. To do this, one must understand the risks, the triggers, and the consequences.
Instructions

Security Systems Risk Management
Write a 3–4 page paper in which you:
Define risk management and information security clearly. Discuss how information security differs from information risk management.
Explain security policies and how they factor into risk management.
Describe at least two responsibilities for both IT and non-IT leaders in information risk management.
Describe how a risk management plan can be tailored to produce information and system-specific plans.
Use at least two quality resources in this assignment. Note: Wikipedia and similar websites do not qualify as quality resources. The Strayer University Library is a good source of resources.
Your assignment must follow these formatting requirements:
This course requires the use of Strayer Writing Standards. For assistance and information, please refer to the Strayer Writing Standards link in the left-hand menu of your course.
The specific course learning outcome associated with this assignment is:
Assess how risk is addressed through system security policies, system-specific plans, and contingency plans.