OSForensics
Describe the software application in detail.
OSForensics is a tool that allows one to identify suspicious files and activities through matching and comparisons of drive signatures, memory, emails, and binary data. It enables an investigator to quickly extract forensic evidence from computers by utilizing indexing and advanced file searching, allowing efficient data management.
How it is used
The first step is creating a case where all the gathered evidence that is related will be stored in an OSF case file to be used later. To make the data tamper-proof, all the data is hashed cryptographically. Once the case files are created, they can be easily exported in HTML and PDF reports that are readable to summarize the evidence found (OSForensics, 2018). Reports that are created outside the tool can be added, and case narratives edited through the HTML editor
The management of the storage devices is done centrally for convenient access all through the OSForensics. This tool can be installed and run from a portable USB drive so that an investigator can take it directly to the target computer without any contamination risks to the valuable data. Using OSForensics, one can take an exact replica of the drive partitions of an active system. This is especially useful when conducting live tests, for example, on servers that cannot be taken offline. Using the OSFClone tool, one can image a drive from a system that is not live.
What evidence does it uncover?
Deleted files
After file deletion, even after it has been removed from the recycle bin in the computer, it still exists until it is overwritten, whereby a new file takes its place on the drive. In an attempt to restore a deleted file to a usable state, OSForensics can track down the ghost file date on the given drive. Each deleted file that the tool finds is given a corresponding Quality indicator between 0 and 100 (OSForensics, 2018), values that are close to 100 show that most parts of the deleted file are intact, with only a few data clusters missing. Additionally, OSForensics can give a graphical view of clusters of the deleted files on the physical disk.
Recent Activity
OSForensics helps investigators determine what a computing device user has been doing. T can uncover the actions performed by the users in the recent period that they used their computer. For instance, it can show the history of the web browsers, the connected network shares and USB devices, and the documents that were opened. It can also scan the operating system and get the website logins and passwords, wireless networks, USB drives, and recent downloads (OSForensics, 2018). The benefit of this is that one can detect the patterns and trends of the user or associated account that they accessed.
System information
OSForensics is able to find out what is inside the computer. Some of the information about a computer that may be of interest include the Installed hard drives, types and the number of CPUs, type and amount of RAM, and any USB devices that have been connected. OSForensics can directly look at what is currently in a system’s main memory. For each process, it can view 47 metadata columns. Hidden disk areas (HPA/DCO) of a hard disk can be discovered using OSForensics in an attempt to expose all sensitive information that would have been otherwise inaccessible.
Emails
Within the email archives used by popular email programs, OSForensics helps in performing full-text searches (OSForensics, 2018). It first indexes the archives in question, which may take some time to allow repeated file searches later, which would be much faster.
How can investigators use this tool to uncover data hidden in computers that have Windows?
On the start menu, you create a case by entering the case name, investigator, organization, and Timezone, and then select your directory. The new case appears in the Manage Case dialog. To analyze a USB drive, you create two text documents in the drive. Make the first document hidden and delete the second one permanently. Hide some more files and delete some in the drive. Go back to the application, select deleted file search, select the USB drive and search (Varga, 2016). The deleted files are found, but a percentage shows the files’ accuracy. The files can now be extracted and saved in a different location.
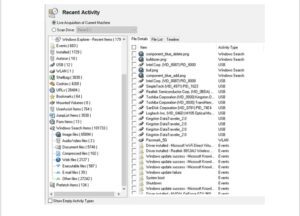
Recent Activities Window
This image shows the recent activity window in OSForensics when used during the determination of the recent activities of the computer.
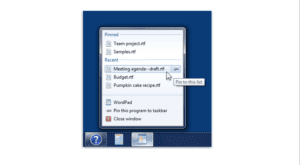
Jump List
This diagram shows the ability of OSForensics to utilize jump lists, allowing easier access to favorites and programs.
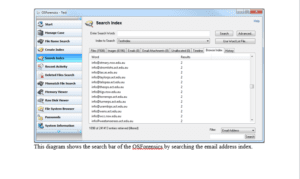
Search Bar
This diagram shows the search bar of the OSForensics by searching the email address index.
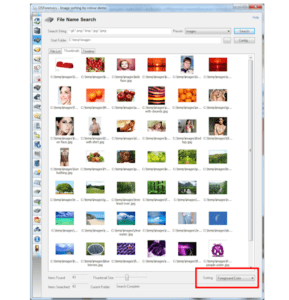
Color Sorting
This diagram shows the ability of the OSForensics to sort pictures by color.
Disk Signatures
This image shows the comparison of disk signatures using OSForensics.
Recommendation
This tool is best suited for situations where time is of the essence, and one tool can be used to gather evidence fast and independently. It only works on Windows platforms, so it is not suited for different platforms.
References
OSForensics. (2018). Discover relevant forensic evidence faster. Retrieved from https://www.osforensics.com/discover.html.
OSForensics. (2018). Identify suspicious files and activity. Retrieved from https://www.osforensics.com/identify.html
Varga, A. (2016). OSForensics Basic Overview Tutorial. Retrieved from https://www.youtube.com/watch?v=CiNGcOz5sO4
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question
OSForensics
Research 1 computer forensics tool for Windows.

OSForensics
In a report of 3–5 pages, complete the following:
- Describe the software application in detail.
- How is it used?
- What evidence does it uncover?
- How can investigators use this tool to uncover data hidden in computers that have Windows?
- Include at least 5 images, and describe each image.
- Make a recommendation on when to use this tool.

