Organization Systems and Network Diagram
Network Diagram
Data Flow Diagram
Explanation
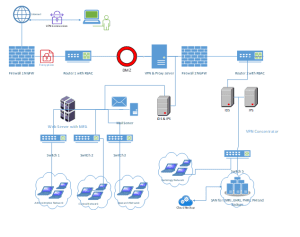
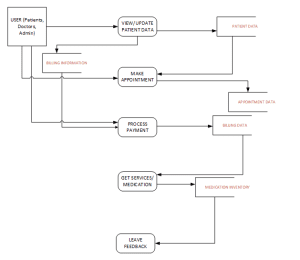
The following network and data flow diagram for Augusta Medical Hospital is designed to show how users, systems, and external entities exchange data in a secure manner that meets regulatory and legal requirements such as HIPAA. It uses layered security to protect patients’ information, and the system cannot be breached or hacked to release the information to unauthorized people. Both the network and data flow diagrams outline how Augusta Medical Hospital maintains the security of patient data and, at the same time, free access to the records of patients, imaging data, and other health services. The network is logically divided to minimize exposure of patient details and organizational data with sub-networks for administration, patient care, research, and radiology use. This segmentation makes sure that only authorized users have access to particular kinds of data in order to minimize cases of intrusion.
Security measures like firewalls, IDS/IPS, DLPs, and encryption are implemented to minimize vulnerability risks posed on the network (Mansikka, 2023). The use of role-based access control, together with multi-factor authentication, ensures that only authorized personnel gain access to the information in the hospital’s network through a secure web portal that is protected by multi-factor authentication. All communications between the user and the web server regarding data are SSL/TLS-protected to ensure PHI security while in transit. This web portal, therefore, lets patients view medical records, manage appointments, pay their bills, and ensure access only by authorized people for the same.
Network Security and Flow of Data
The network is firewalled and filters both inbound and outbound traffic. An Intrusion Detection/Prevention System (IDS/IPS) protects against malware activities. All the traffic must go through these security layers before reaching the internal systems of the hospital. This ensures threat mitigation at the perimeter.
Internal System Architecture
The web server moves data to the application servers, which process the business logic for EMRs, EHRs, and other patient information systems. They communicate with the database servers, which store patient information securely. At each step, transit-encrypted data through TLS and at-rest AES-256 encryption ensures it is protected during every stage in the process (Rutter et al., 2017).
Compliance and Protection of Personal Data
This system uses RBAC to control access to relevant sensitive data based on the user’s role within the organization. This means that only properly cleared personnel will be able to view or edit patient records. This access will be logged and monitored for compliance, providing the full audit trail, which is important for regulatory compliance.
The hospital has a regular backup and disaster recovery system, including off-site storage of the backed-up data in a safe location. These backups are encrypted for data protection to support the HIPAA requirements for disaster recovery (Barnoschi, 2018). Therefore, in the event of ransomware attacks or system failure, the hospital can quickly restore the systems without any problem in attending to the patients.
References
Barnoschi, A. (2018). Backup and disaster recovery for modern enterprise. In 5th International Scientific Conference, Business and Management.
Mansikka, J. (2023). Data loss prevention: For securing enterprise data integrity.
Rutter, R., Lauke, P. H., Waddell, C., Thatcher, J., Henry, S. L., Lawson, B., & Urban, M. (2017). Web accessibility: Web standards and regulatory compliance. Apress.
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question
Understanding how data flows within the system is one of the key aspects for knowing how to secure and segment the data based on the classification level. Create a system design diagram that demonstrates how data flows within the system and include a network diagram that has all the required regulatory security controls, network security devices, and the systems’ interconnection for Augusta Medical Hospital.

Organization Systems and Network Diagram
Part 1: Network Diagram and Data Flow Diagram
Illustrate how data flows within the business application system using Visio or similar diagramming software. Within the system and network portal diagram, you will show how the web portal is compliant. Be sure to address the following in the diagrams:
- Display the organization’s technical requirements.
- Display the compliance of associated servers, routers, access-control components, data storage, internal and external data communication, data backup, email servers, point of sales, thin clients, and so forth.
- Identify related systems and assets, regulatory requirements, and overall risk approach.
- Demonstrate each IT task to the next as aligned to regulations/compliance. For example, start with the user logging in and then go through each step and validate it.
- Evaluate the implications of the system connectivity to the internet.
- Evaluate if the systems have a data classification and how data is protected in transit, processing, and at rest.
Part 2: Explanation
In 250-500 words, explain the network diagram and how you addressed the diagram components listed in Part 1. Submit the diagram and explanation on one document.