Network Design and Implementation
Computer networks have become vital in the running of modern organizations as they are used for communication, data management, and the creation of backups in case of a catastrophic event. It is thus important for any organization to ensure its network is secure and working at optimum levels. In order to achieve this objective network, monitoring has to take place. Some of the tools used by network administrators to monitor a particular network’s health include simple network management protocols commonly known as SNMP, NetFlow, and Syslog. In this case study, we shall discuss the requirements and how to set up the network monitoring tools in a five-department office in a two-story building that uses Ipv4. All the server software listed above requires the user to download a copy of the manual in order to understand the installation process or have the required technical skills (Lee, Levanti & Kim, 2018).
A simple network management protocol is an internet protocol that utilizes IP addresses to organize and monitor devices on a network. The protocol works by installing software or agents on computers in the network, and the software then reports the status of the network to administrator computers. In order to install the protocol, the first step is to have a network connection within the office; this can be either a wired or wireless connection. The network connection should also be using Ip addresses for the identification of devices. Some of the devices that can be used on the protocol include routers, servers, and personal computers. It is also a requirement that new IP addresses be created after the installation of the SNMP protocol. The network administrator also has to select which ports the protocol is going to use and leave them open. The application protocol also requires skilled individuals to set up. The hardware requirements for installing SNMP software include a minimum of 512Mb of RAM, at least 3Mb of hard drive space, but 10Mb would be more effective, and a 1 GHz processor for the 32-bit version and 1.4 GHz for the 64-bit version of the software (Boyko, Varkentin & Polyakova, 2019). Higher computer resources would work more smoothly for the software but are not a requirement.
NetFlow analyzer is a system software that can be used for the monitoring and improvement of networks. The software has both hardware and technical requirements. Some of the hardware requirements include a minimum of 4Gb of RAM, a minimum 3.2Ghz Quad-core processor, and a 32-bit computer with a hard disk of at least 500Gb set up with Raid0. If the network has more than 5000 interfaces to be monitored, the minimum requirements will increase to 16Gb of RAM on a 64-bit operating system (Campazas-Vega et al., 2021). The software supports almost all modern web browsers. The software supports routers, servers, and modems. However, if the Cisco version of NetFlow is used, all the devices have to be Cisco models, or else the software will develop errors. NetFlow can be used on various network infrastructures, such as wired and wireless networks that support either Ipv4 or Ipv6. The analyzer software is used to monitor networks by sending reports in the form of network packets to the administrator. The software can be used for the identification of any errors or disconnections within the network, making network analysis easier for the administrator.
Syslog is the other software server software that can be used for network monitoring. The hardware requirement for Kiwi Syslog server software includes a minimum of 2Gb RAM, 350Mb of hard drive space, and at least a 1.2Ghz dual-core processor. The software will, however, require more hardware specifications if it is to be used for monitoring a large network. The server software runs on Windows 10, 8.1, and 8, with lower operating systems being incompatible. Windows Server 2016, 2012, and 2012 R2 are also supported by Kiwi Syslog server software. The software also supports a limited number of database software such as Microsoft Access, MySQL, and Oracle. The supported SQL database versions include Microsoft Server 2012, 2014, 2016, and 2017. The default port for the Syslog server is port 514, and one more is selected by the user under the UDP protocol. Port 25 is used as the default outbound port working under the TCP protocol. Other ports used by Kiwi Syslog server software include ports 8088, 3300, 6514, 162,163, 6514, and 1468 (Vaarandi, Blumbergs & Kont, 2018).
The changing and movement of network cables and devices might require more than one person since the organization’s space covers a large area. The administrator needs to identify and set up the main computer that will act as the main server. This computer needs to be located in a central location, away from easy access by unauthorized users, as a security measure. It is also required that the organization provide a specific time when their network will have to be stopped in order for modifications to occur. This can be on the weekend or during the night when other employees are not busy utilizing the network. A contingency measure is also required in the event that the installation procedure does not go smoothly. The network administrator will also have to create a budget in order to know which resources will be allocated for which purpose.
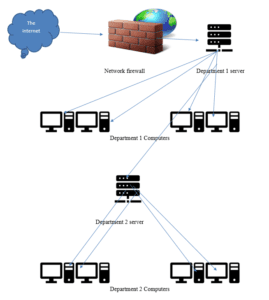
The network architecture will be drawn on a network diagram in order to better understand the arrangement of network devices and how the network monitoring software servers will function (Kirk, 2021). The diagram will depict the two-story building with each floor being drawn below the other and the ground floor working as the first diagram. Routers, switches, and servers are usually depicted using common icons that are identifiable without the use of labels.
Ground Floor Network Diagram
The above network architecture shall be used for the first floor with a slight modification to include another department office within the network. According to the network diagram, the first point of contact between the internet and the internal network is a firewall. This is to ensure viruses, malware, and malicious users on the internet are kept away and the network is afforded an extra layer of security. Once the internet connection has passed through the firewall, it is passed to the main server, which then distributes the connection to other computers and devices on the network. It is this specific server that should act as the administrator server where the entire network monitoring software should be installed. This server would work perfectly because all other computers and network devices have a connection to the computer. When a threat is detected on the internet, it is also easier to shut off the internal network from the internet from this point.
References
Boyko, A., Varkentin, V., & Polyakova, T. (2019, October). Advantages and Disadvantages of the Data Collection Method Using SNMP. In 2019 International Multi-Conference on Industrial Engineering and Modern Technologies (FarEastCon) (pp. 1-5). IEEE.
Campazas-Vega, A., Crespo-Martínez, I. S., Guerrero-Higueras, Á. M., Álvarez-Aparicio, C., & Matellán, V. (2021, September). Analysis of NetFlow Features’ Importance in Malicious Network Traffic Detection. In Computational Intelligence in Security for Information Systems Conference (pp. 52-61). Springer, Cham.
Kirk, A. (2021). Network Diagram. SAGE Publications, Ltd..
Lee, S., Levanti, K., & Kim, H. S. (2018). Network monitoring: Present and future. Computer Networks, 65, 84-98.
Vaarandi, R., Blumbergs, B., & Kont, M. (2018, April). An unsupervised framework for detecting anomalous messages from syslog log files. In NOMS 2018-2018 IEEE/IFIP Network Operations and Management Symposium (pp. 1-6). IEEE.
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question

Network Design and Implementation
You have been hired as an experienced network engineer to design a network that will integrate SNMP, Netflow, and syslog to monitor network health. The wired network consists of five departments in a two-story building using IPv4 currently. Research and create a list of requirements for deploying SNMP, Netflow, and syslog into the network with minimal impact on users and customers. Including all three services in the network may require new IP addresses to be allocated. Make sure new IP addresses are listed in the requirements.
Write a minimum 4-page paper and draw a network diagram that will be inserted into your plan to present to your manager, who has a technical background, that details your plan and your timeline for implementation.