IT Management Presentation
Hello, and welcome to my presentation. The primary aim of this presentation is to get my team informed on the required information when selecting IDS software.
Highlighted above is an outline of the presentation. The presentation will begin by defining the network intrusion and how it works. This would then be followed by explaining what an intrusion detection system is and the purpose of such a system in an organization. The next slides will then explain four common types of intrusion detection systems and briefly elaborate on the four latest and most popular software. I will then finalize my presentation with a summary of what is involved in the selection of an IDS and four best practices for the success of the IDS.
A network intrusion is any illegal action performed on a network platform connected to the internet. In many scenarios, network incursions often involve the theft of valuable network resources after the network security has been compromised. In this regard, there is a need for organizations and their cyber security teams to comprehend how network intrusions are conducted, ways of detecting their presence, and the response mechanisms that can be adopted for the prevention of these attacks on the network. Network intrusion may occur in different ways (Contributor, 2019). One of the ways through which network intrusion takes place is through scanning attacks. This form of network intrusion involves sending data to the network to collect information about the topology of the network, types of permitted traffic, open or closed ports, or the version of software running on the network. SQL injection attacks fondly use this scanning technique to locate vulnerable points on the network. Asymmetric routing is the other way through which network intrusion occurs on the network. It refers to when the packets use different routes while travelling to their destination and then back. Based on this functionality, the attackers may use asymmetric routing behaviors to pass malicious packets across certain parts of the system, bypassing the security setups executed on the network (Contributor, 2019). Permitting the network to perform asymmetric routing means that an organization is open to SYN flood attacks. Buffer overflow attack is the other way through which network intrusion may occur, resulting in infiltration on the memory components of the devices belonging to the network. A buffer overflow happens when a vast amount of data is allocated to the buffer that can be handled at a certain duration hence causing the data to overflow into adjacent memory (Contributor, 2019). Network intrusion may also occur through protocol-specific attacks or traffic flooding.
Intrusion detection systems are categorized as security systems that are geared toward protecting information systems. The systems work with authentication access control measures to provide the network with a double layer of protection against attacks. This system is often utilized alongside antivirus or malware software that provides enough computer device security. The intrusion detection system provides an additional level of protection against dangerous forms of malware (Pratt, 2018). The IDS has the ability to capture snapshots of the whole system together using the intelligence that has been gathered from developed patterns to determine the time of occurrence of the attack or provide an evaluation of how the attack occurred (Pratt, 2018). Some of the vital components of intrusion preparation include information on the potential intrusions, ways of curbing these intrusions from happening and being at par with the active and past intrusions that have been recorded. While organizations may find that it is too late when an attack has already taken place, understanding the type of intrusions that have occurred or have been attempted in the past is critical in preventing the occurrence of future attacks (Pratt, 2018). Understanding the extent of an attack’s intrusion is also vital while deploying response mechanisms to address security concerns on the system.
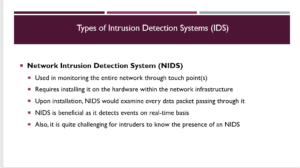
The leading type of intrusion detection system is the network intrusion detection system, which monitors the organization’s entire network through one or more touch points. For effective utilization of NIDS, one would be required to install some sections of the hardware within the network infrastructure. Upon installation, the NIDS can sample every packet that passes through it. Performing this role may result in the system failing to detect the occurrence of an intrusion attempt on the network. Besides this, NIDS is beneficial because it examines both inbound and outbound traffic located in strategic locations, permits the detection of events on a real-time basis, and is more challenging for intruders to detect the presence of this system on a network. The only downsides of this system are its low specificity and hands-on maintenance.
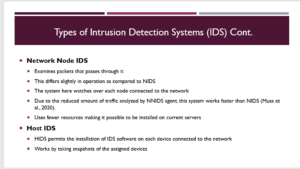
The NNIDS (Network Node Intrusion Detection System) varies slightly from a NIDS. This system works by evaluating the packets that pass through it. Nonetheless, as opposed to relying on the central device to monitor the traffic on the network, it examines every node that is connected to the network. There are two broad benefits of using the NNIDS. One of these benefits is that it necessitates higher speeds since the quantity of traffic being analyzed by each NNIDS agent is greatly reduced. The reduced amount of traffic ensures that the system works at a faster rate as opposed to using the other types of IDS. The other benefit is that this system takes up fewer resources, making installation on the current servers easier (Musa et al., 2020). NNIDS calls for multiple installations even though the agents report to a central dashboard. Apart from this, the other type of IDS is the host intrusion detection system which takes the device independence of NNIDS to a higher level. HIDS permits the installation of IDS software on every device that is connected to the organization’s network. This type of IDS works by taking snapshots of their assigned device, whereby a comparison of current and past records could indicate the occurrence of an intrusion (Musa et al., 2020). In this regard, HIDS are advantageous because they can be plugged into computers or servers, highlight the affected devices, and can easily notify administrators if files have been modified or deleted (Musa et al., 2020). Despite these advantages, the HIDS can also suffer from “after-the-fact” monitoring that causes the system to respond slowly.
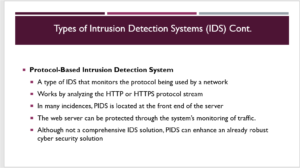
The fourth type of intrusion detection system is the protocol-based intrusion detection system. This system works by monitoring the protocol in use. It examines the HTTPS protocol stream that exists between the devices being used and the server. In many instances, the PIDS is located on the front side of the server. This system can offer protection to the web server by monitoring both inbound and outbound traffic (Pratt, 2018). Since this system focuses on the protocol, they are hardly considered a comprehensive IDS solution. On the contrary, PIDS can often be used to augment an already robust cybersecurity solution.
One of the popular IDS software is SolarWinds security event manager, which works on HIDS. This software examines the USB devices and files that come into the network and whether they contain any malicious modification. Also, the SolarWinds security event manager can check the file system to determine that files have not been deleted or relocated to unusual locations. The other popular software, Suricata, uses complete signature language to outline all the available threats. Suricata works to examine multi-gigabit traffic. The software can detect protocol on any port and apply detection logic on each packet as it passes through. Snort, another popular and the latest IDS software is utilized for packet sniffing and intrusion detection. When the software’s three modes are combined, snort can be used as an IDS and an IPS (Contributor, 2019). This software can detect attacks such as SMB probes, buffer overflows, stealth port scans, and OS fingerprinting attempts. The last popular software is OSSEC which focuses on the log files and changes in the file system that occurs on the computer. This software takes a snapshot of the system and logs files to determine if any transitions have occurred and their legitimacy. It also monitors if any attempts have been taken to modify the root account on the Unix system.
I selected the NNIDS because its functionality is closely related to NIDS. However, the only variation with this type of IDS is that it can only be executed on one host at a time as opposed to the entire subnet. There are four best practices that should be considered in the selection of software to guarantee its success during utilization. The first best practice is for the organization to outline what normal behavior looks like for the network. This practice is important as it aids in the determination of what malicious behavior looks like. The other practice for success is changing defaults where necessary since each network is bound to vary (Musa et al., 2020). The selected IDS should be knowledgeable of all the relevant devices and applications, together with critical points of security. In this regard, using custom devices often requires an organization to design its IDS differently from what is suggested in a manual or guide. The third practice for the success of an IDS is to ensure that the IDS has been placed correctly. Users should ensure that they have deployed it at the highest point of visibility to ensure that it is not overwhelmed with data. The common method of deployment is at the back of the firewall but on the edge of the network (Musa et al., 2020). Also, the user may consider installing multiple IDS in an attempt to deal with intra-host traffic. The last practice is to ensure that one has a clear and explicit understanding of device inventory together with what is on the network. Comprehending all the available components, their roles, how they function, and their vulnerabilities helps set up the IDS correctly.
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question
Scenario: You are given the responsibility to select and implement an Intrusion Detection System (IDS) for your management team. The goal of the presentation is to inform and move your team to act on the next step which is selecting an IDS software.
For additional information on IDS, refer to the following: What is an intrusion detection system? How does an IDS spot threats, and what is an intrusion detection system? Latest Types and Tools

IT Management Presentation
Using the white papers and researching the topic, recall the role of the IDS prevention system in defending networks.
Prepare an 8- to 10-slide presentation using PowerPoint, and include the following slides:
Definition Slide: What is Network Intrusion and how does it work?
Explanation Slide: What is an Intrusion Detection System and what is its purpose?
Types of Intrusion Detection Systems Slide: Describe 4 common types.
IDS Software Slide: List and briefly describe the 4 latest and most popular Software.
Next Steps Slide: Identify an IDS. Write a summary of what is involved with selecting software. Describe 4 best practices for success of the IDS.
Cite any sources to support your assignment.
Format your citations according to APA guidelines.