IPv6 Internet Protocol
Compose an executive summary highlighting the paper’s contents and reasoning for your chosen topic.
IPv6 is the latest internet protocol taking over from IPv4 to solve the issue of limited addresses. In addition to improving internet efficiency, IPv6 offers a vast address space to accommodate growing internet usage. The strategic analysis of IPv6 indicates that the new protocol enjoys ample address space, routing effectiveness, and improved internet service quality. Additionally, the new protocol offers opportunities to improve the operations of organizational information systems, lower information system costs, and the fusion of services. However, the deployment of IPv6 is hindered by non-compatibility and lack of literacy among internet users, which may stimulate resistance. The deployment of IPv6 raises some ethical and legal concerns regarding the security of a large amount of information on the internet, governance of the internet, and the possibility of misuse of the new protocol. In the past few years, IPv6 has witnessed a great improvement regarding standardizing devices in readiness for the new protocol. The new internet protocol promises a brighter future for internet users with an increase in the efficiency of the internet and ample address space. China and Japan are among the countries that have taken the opportunity to deploy IPv6 early enough to reap its many benefits.
Are you interested in an original copy of “IPv6 Internet Protocol”? Contact us
Networking
Internet Protocol version 6, represented by IPv6, is the latest. The Internet Engineering Task Force developed IPv6 to solve the exhaustion of addresses in IPv4 (Oracle, 2020). Additionally, the new internet protocol improves the capability of the internet by enhancing the quality of internet services, simplifying header format, auto-configuration of address assignments, and supporting cyber privacy. An analysis of IPv6 is carried out in this paper to determine its strategic viability, ethical and legal concerns, and current and future position in cyberspace.
Conduct a SWOT analysis by analyzing the chosen topic’s strengths, weaknesses, application opportunities, and threats from competitors.
Strengths:
Supports a large number of internet users
The significantly larger address space of IPv6 allows unlimited growth of internet users (Kunc et al., 2012). As such, it could better serve organizations with large internet users and those that expect the numbers to keep growing.
Improved effectiveness in routing
The hierarchical arrangement of addresses in the IPv6 decreases the size of routing tables significantly (Kunc et al., 2012). As a result, there is an increase in the equipment’s functioning period, improving the routing’s effectiveness.
Improved quality of services and security
IPv6 provides a direct connection between optional nodes, improving the effectiveness of multimedia applications and enhancing the safety of the system applications (Kunc et al., 2012). Additionally, there is the mobility of system nodes, which improves the quality of IPv6 services and enhances their security.
Weaknesses:
Non-compatibility
The current hardware and software are designed for IPv4, which is not directly compatible with IPv6 (Kunc et al., 2012). Therefore, organizations will likely suffer a cost in acquiring hardware and software entirely compatible with the new internet protocols.
Resistance to change among Internet users
Some internet users doubt replacing IPv4 with IPv6 (Kunc et al., 2012). They argue that IPv4 has proven to be adjustable and offers the best internet services. It may take some effort to convince the users of the usefulness of IPv6 over IPv4.
Opportunities:
Information systems operations improvement
There is an opportunity to enhance the functioning of information systems by developing improved applications under IPv6 (Kunc et al., 2012). As such, organizations adopting IPv6 would enjoy the economic value of internet services.
Lower IS operations cost
There is an opportunity to reduce the cost of running organizational information systems by surrendering some operations to the network layer. Some processes that could be surrendered to the network layer include privacy functions, authentication, and integrity of organizational data (Kunc et al., 2012). Such services could be achieved by AH and ESP protocols under IPv6.
Fusion of services
The mobility of nodes in IPv6 could offer an opportunity for the fusion of services (Kunc et al., 2012). As a result, employees could access business-level features from wherever they are, improving the effectiveness of remote working.
Threats:
Incompatibility of IPv6 protocols with the existing technologies
The deployment of IPv6 could present challenges due to a lack of support for certain functionalities and incompatibility issues (Meena & Bundele, 2015). The incompatibility issues of IPv6 with the current hardware and software threaten its implementation as some managers may not be willing to spend cash on acquiring new technologies.
Resistance among Internet users
Most internet users are accustomed to IPv4 and are experienced using this internet protocol. Thus, they may resist change to IPv6. Additionally, most organizations have not tried enlightening their staff on IPv6 (Meena & Bundele, 2015). Lack of enlightenment and the fear of the unknown may lead to massive resistance to IPv6 among internet users.
Evaluate the current ethical and legal concerns surrounding your topic.
There are four major categories of ethical and legal concerns surrounding IPv6. The types include the right to internet domain names and internet use, the security issues of ipv6, the applications of the technology, and issues related to governance.
Equal right to domain names and internet use
Legal and ethical issues exist over the right to domain names and internet use. Is it ethical to deny an entity a domain name that another entity has taken? Is it ethical to allow some internet users to access information inaccessible to others? These questions center on the viability of IPv6 concerning the right of individuals to express and access information. IPv6 provides a larger internet space, allowing the number of internet users to expand. With the increased number of internet users, there are questions about the right to domain names, especially when two or more individuals claim the same name (Zielinski, 2006). The larger internet space provided by IPv6 means that more companies and individuals will seek to establish a web presence, some of which may share names. There could be ethical and legal issues for individuals and firms to be denied a right to use their names simply because another entity has taken them. With IPv6 removing restrictions and allowing everyone to get on board, it is necessary to get a solution to the domain name issues to avoid battles among companies and firms that share names.
Security concerns
Implementation of new technology always comes with security concerns. The security of information on the internet raises both ethical and legal issues. While accessing other people’s data without permission is illegal, internet users must maintain ethics and respect other users’ interests. With IPv6 increasing the number of entities accessing the internet, there are likely to be many security cases accompanying this new internet protocol (Rubens, 2012). IPv6 tries to solve the issue of security by allowing end-to-end transmission. However, the security question cannot be said to be wholly sorted, as many new users brought to the board by IPv6 will likely fall prey to malicious internet users. The likelihood of a surge in security cases brings legal authorities into the mix. Information technology experts have a role in sensitizing new users to ensure their information is secured while using the internet. Additionally, ethics demand that internet users should respect the legitimate interest of others.
Concerns over the Application of IPv6
The use of IPv6 is likely to raise new ethical issues and changes in the laws to accommodate the new scope of applications not covered under IPv4. IPv6 offers an improvement of IPv4, which enables technology uses that would not be possible under IPv4. As such, there may be some IPv6 application concerns centering on security, implantation of chips on individuals, collection and storage of huge amounts of data, and the individual unique identification system (Zielinski, 2006). Some individuals may have concerns regarding applying this new internet protocol as it may contradict their ethical standards. Consider using IPv6 to implant chips in individuals and collect their information for storage in online databases. What if malicious individuals access the information? More ethical concerns relating to the application of IPv6 will unfold as the technology is implemented. The new internet protocol will undoubtedly impact how people operate at their workplaces. It will likely spark changes in internet security laws to protect internet users’ information.
Select one ethical or legal concern surrounding your topic, take a position, and provide a rationale.
IPv6 Governance concerns
As IPv6 expands internet usage, the governance issue becomes more significant. Whoever controls the internet will be more powerful than any political leader, even from the most potent countries (Zielinski, 2006). The legal and ethical issues surrounding IPv6 internet governance entail how they get the power and what they do with it. Will everyone have a say in the management of the Internet? Will it marginalize some groups over others? The Engineering Task Force (ETF) is not accountable to anyone, presenting strengths and weaknesses. It is argued that self-regulation is stronger in accountability than having explicit laws regulating people. On the other hand, this leaves one wondering whether there are rules, how they were established, and who enforces them.
The solution to IPv6 Governance Concerns
Traditional static governing bodies or regional institutions cannot handle many issues in IPv6 cyberspace. IPv6 governance requires a less hierarchical cooperation structure among the standard developers, network operators, internet service providers, regional governments, and internet users (Georgia Institute of Technology, 2020). Collaboration among these different players will solve the problems accompanying the widespread use of the internet while at the same time maintaining the openness and interoperability required in IPv6 cyberspace. As much as the rules of territorial governments shape the use of the internet in that territory, frequent technological changes produce new regulatory bodies to respond to the new demands of technology.
Analyze the improvements to your communication technology topic over the last two years, and suggest an improvement based on its current usage.
IPv6 has been ‘the future technology since 1998 (Internet Society, 2017). Currently, many countries are working on the implementation of IPv6. For instance, all three major mobile networks in Japan, including Softbank, KDDI, and NTT, have been working on deploying IPv6 for the past two years. JIO’s rollout in India has driven the country’s traffic measure to exceed 20 percent (Internet Society, 2017). The increased deployment of IPv6 technology in different countries is due to increased enlightenment concerning the new internet protocols and the growing need for internet services in businesses and personal use.
Improvements have been witnessed in smartphones and computers to enable users to access the website and carry out internet operations using IPv6. The applications of users’ devices, computers, and smartphones have experienced tremendous improvement to accommodate the new Internet protocol (Internet Society, 2017). Other improvements have been witnessed in the servers, server network, and the applications running on the server. Additionally, there have been efforts by the user upstream network providers and the server upstream network providers to ensure compatibility with IPv6.
Mobile network providers are currently taking steps to rum IPv6 only where they can. The providers face a tradeoff in deciding whether to pay for IPv4 or IPv6 Access Point Names (APNs) since the payments are made separately (Internet Society, 2017). Mobile network providers report that between 70 and 90 percent of their traffic is IPv6. Internet Service Providers have as well reported a significant reduction in their costs following the deployment of IPv6. Some companies are working on standardizing their systems to IPv6 requirements (Internet Society, 2017). The companies standardizing IPv6 include ZigBee Secure Energy Profile 2.0, the OpenThread Group, and the Open Connectivity Foundation.
Predict the future role of the communication technology you’ve selected for personal and commercial use.
The future of internet space belongs to IPv6, and firms need to standardize their hardware and software in preparation for IPv6. IPv6 deployment has gained momentum over the past years, especially in Japan and China (IPv6, 2020). The countries have already put in place projects that rely on the new internet protocols and look forward to future development. In the coming few years, IPv6 will take over the internet space, and the countries that adopted the new internet protocols earlier will benefit most.
IPv6 significantly improves internet speed, which is essential as internet use grows over the years. The implementation of IPv6 in China has revealed that the new internet protocol has great potential for the future of the internet. For instance, the latest internet protocol has enabled China to move data around the internet at about 100 times the internet speed (IPv6, 2020). Additionally, IPv6 has the potential to drive innovations and push through technology deals. A good example is a deal involving a British company, Spirent Communications, which China chose as a new test solution routers provider.
IPv6 will stimulate the connection of many devices on the internet, making it possible to monitor and ease the operation of devices. Japan has demonstrated the hope presented by IPv6, with Yokohama Trials as one of the major IPv6 showcase projects. Over 300 vehicles in Tokyo, including taxis, trucks, and buses, are continuously connected to the internet (IPv6, 2020). The users can monitor traffic conditions, including the speed of their vehicles, the conditions of the roads, and the weather. Connecting such a huge number of vehicles to the internet would not be possible without IPv6.
Create a diagram that illustrates the communication structure of your chosen technology in Visio or its alternative open-source software. Note: The graphically depicted solution is not included in the required page length.
Diagrammatic Representation of IPv6 Communication Structure
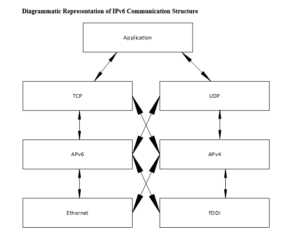
Diagram
Similar Post: Memo Feedback
References
Georgia Institute of Technology. (2020). What Is Internet Governance? | Internet Governance Project. Internet Governance Project. https://www.internetgovernance.org/what-is-internet-governance/#:~:text=Internet%20governance%20refers%20to%20the,UDP%2C%20DNS%20and%20BGP).
Internet Society. (2017). State of IPv6 Deployment 2017 | Internet Society. Internet Society. https://www.internetsociety.org/resources/doc/2017/state-of-ipv6-deployment-2017/.
IPv6. (2020). IPv6 – The Future of the Internet | IPv6.com. IPv6.com. https://www.ipv6.com/general/ipv6-the-future-of-the-internet/#:~:text=The%20transition%20to%20IPv6%20holds%20the%20future%20of%20the%20internet%20infrastructure.&text=One%20of%20the%20important%20aspects,bit%20addresses%20used%20by%20IPv4.
Kunc, U., Pepelnjak, I., Sterle, J., Istenič, M., Kobal, A., & Lisec, S. et al. (2012). : Transition to IPv6 (Guidelines for Deliberation on the National IPv6 Strategy). Go6.si. https://go6.si/docs/Study_MVZT_IPv6_en.pdf.
Meena, R. & Bundele, M. (2015). A Review on Implementation Issues in IPv6 Network Technology. International Journal Of Engineering Research and General Science. 3. 800-809. 10.13140/RG.2.2.14111.51363.
Oracle. (2020). Chapter 1 IPv6 (Overview) (IPv6 Administration Guide). Docs.oracle.com. https://docs.oracle.com/cd/E19683-01/817-0573/chapter1-1/index.html.
Rubens, P. (2012). 7 IPv6 Security Risks. Esecurityplanet.com. from https://www.esecurityplanet.com/network-security/7-ipv6-security-risks.html.
Zielinski C. (2006) Social and Ethical Aspects of IPv6. In: Zielinski C., Duquenoy P., Kimppa K. (eds) The Information Society: Emerging Landscapes. IFIP International Federation for Information Processing, Vol 195. Springer, Boston, MA
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question
Term Paper: Networking
Due Week 10 and worth 200 points

IPv6
Select one of the following topics on which you will base your responses in the form of a term paper:
- Network Neutrality
- Web 2.0
- Wireless Technology
- Broadband Convergence
- S. Telecommunication Policy
- Internet Security
- IPv6
- WWAN
- WLAN
- DNSSEC
- WAN
Write a fully developed paper in which you:
- Compose an executive summary highlighting the paper’s contents and reasoning for your chosen topic.
- Conduct a SWOT analysis by analyzing the chosen topic’s strengths, weaknesses, application opportunities, and threats from competitors.
- Evaluate the current ethical and legal concerns surrounding your topic.
- Select one ethical or legal concern surrounding your topic, take a position, and provide a rationale.
- Analyze the improvements to your communication technology topic over the last two years, and suggest an improvement based on its current usage.
- Predict the future role of the communication technology you’ve selected for personal and commercial use.
- Create a diagram that illustrates the communication structure of your chosen technology in Visio or its alternative open-source software. Note: The graphically depicted solution is not included in the required page length.
- Use at least eight quality resources in this assignment. Note: Wikipedia and similar websites do not qualify as quality resources.
Your assignment must follow these formatting requirements:
- Be typed, double-spaced, using Times New Roman font (size 12), with one-inch margins on all sides; references must follow APA or school-specific format. Check with your professor for any additional instructions.
- Include a cover page containing the assignment title, the student’s name, the professor’s name, the course title, and the date. The cover and reference pages are not included in the required length.
- Include charts or diagrams created in Visio or Dia. The completed diagrams/charts must be imported into the Word document before submitting the paper.
The specific course learning outcomes associated with this assignment are:
- Evaluate the need for information communication in the business environment.
- Evaluate the basic technology of information communication.
- Analyze the roles of the internet and the basic protocols that are the foundation of the internet and address the critical issue of quality of service (quality of service).
- Analyze the technologies and architectures developed for networking over shorter distances.
Grading for this assignment will be based on answer quality, logic/organization of the paper, and language and writing skills, using the following rubric.
By submitting this paper, you agree: (1) that you are submitting your paper to be used and stored as part of the SafeAssign™ services by the Blackboard Privacy Policy; (2) that your institution may use your paper by your institution’s policies; and (3) that your use of SafeAssign will be without recourse against Blackboard Inc. and its affiliates.

