Incident Response Exercise and Report
- Contact information for the Incident Reporter and Handler
Name: General
Role: Penetration Tester
An organizational unit (e.g., agency, department, division, team) and affiliation: Red Team
Email address: [email protected]
Phone number : (833) 365-227
Location: 1309 East 7th Street Austin, Texas 78702
Do you need an Original copy of the “Incident Response Exercise And Report”? Feel free to contact us.
- Incident Details
Server access through an unprotected network
An unprotected network most often refers to an open wireless network; however, in the case of the network to the R&D servers, the network is made of fiber optic cables. There has been much research and development in data communications security; wired LAN security has been underestimated. The network to the R&D servers did not have a firewall filter; as such, all traffic was allowed to pass through to the servers. The traditional approaches to securing a LAN are ineffective today, including IPSec and firewalls (Khoussainov & Patel, 2000). An assumption is that the unprotected network did not have proper encryption mechanics, and m or encryption was not present. The architecture presented in Figure 2 allows for launching attaches from the internet directly to the R&D servers.
Un-encrypted data at rest
Following successfully exploiting the unprotected network, the Red team accessed the servers and stole all the design documents. This shows a flaw in the authentication mechanism of the servers. Authentication is determining that a user is who they claim to be. The most common form of authentication is using passwords. However, there are better ways of verifying that a user is legitimate. Passwords are only basic and can be cracked or stolen. Such is the case for the R&D servers. Although the network was successfully compromised, access to the servers was supposed to be impossible for an attacker. 2-factor authentication, for instance, would slow down attackers if it was in place. This can only mean that the authentication mechanism that the servers used was a very basic one.
The penetration testers found it easier to access the server because it was not tightly locked up. Additionally, we can assume that the user accounts were operating with excess permissions. After getting access to the server, the attackers could copy files from the server. This should not have been the case. Even after successfully accessing the servers, the attackers should have had the least privileges, such as listing file directories, not even the capability to view the files. In this case, however, the attacker could steal the files from the servers.
Social Engineering
This exploits human weaknesses to access a computer information system or network. The employees at Sifers-Grayson were prone to exploitation, as seen in the drive that penetration testers left at the lunch table at the headquarters buildings. The employees unthinkingly went ahead and inserted the drive into their computers. The behavior of employees can have a significant impact on the security of an organization’s information system. Most often than not, employees do not view themselves as part of the security of their organization’s information system. The culture of information security should be continuously improved. The social engineering technique that was used in this scenario is baiting. Baiting is analogous to a real-world Trojan horse. The bait can be physical media that rely on a victim’s greed or curiosity. When executing this social engineering, an attacker usually leaves disks or flash drives containing malware where the targeted employees will find them. A curious employee will install and insert the drive into their computers so that malware will be installed.
Another aspect of social engineering that was used may have been tailgating. This is where an attacker seeks entry to a restricted and secured area by simply walking behind someone with legitimate access. Such areas are usually access controlled by biometric authentication or RFID card. Due to the courtesy that most people have, the authorized person may hold the door open for the attacker. The attacker may also ask the employee to hold the door open for them. Due to several reasons, the employee may fail to ask for any form of identification. They may readily accept the attacker’s assertion that they have lost or forgotten their identity document. Once inside the data center, the attackers can install any malware or carry out their activities.
Missing or outdated Antivirus
The social engineering attempt through baiting was successful because the computer devices of Sifers-Grayson were not protected either. The basic assumption and reasonable explanations are that the computers had no anti-malware protection or were outdated. Unless a computer blocks infections, compromises that are auto-running media-hostile devices can cause can be used. A removable media containing malware can be left in a conspicuous place. When inserted into devices, the host computer gets infected alongside the entire network.
Due to the missing anti-malware software, therefore the attackers were able to compromise the PROM burner in DevOps labs. As a result, the malware compromised the AX10, a test vehicle being tested. During the trials, the malware made a cellular phone call to the Red Team, and they successfully took control of the test vehicle and landed it safely in a parking lot at Sifers-Grayson headquarters.
Causes of the Incident
The network connections of Sifers-Grayson were not secured. The network to the R&D did not have any network barrier, and the link to the internet went directly to the servers without any firewall to filter the traffic. Because the network was labeled as unsecured, there was no IPSec in the network either. The connection is not encrypted; therefore, any man-in-the-middle attacks can be launched on the network.
Due to the successful exploitation of the unprotected network, the Red team accessed the servers and stole all the design documents. This shows a flaw in the authentication mechanism of the servers. Access to the servers was supposed to be made impossible for an attacker. 2-factor authentication, for instance, would slow down attackers if it was in place. This can only mean that the authentication mechanism that the servers used was a very basic one. The user accounts were operating with excess permissions. After getting access to the server, the attackers could copy files from the server. This should not have been the case. Even after successful access to the servers, the attackers should have had the least privileges, such as listing file directories, not even the capability to view the files. The fact that the penetration testers could steal the data shows excess permissions.
The successful social engineering exploits showed that the employees had never received any security training. The employees fell to the exploits of the testers unthinkingly. The first test was the flash disk left at a lunch table for the employees. The employees inserted the flash drives into their machines and infected the networks and computers. The second social engineering attack was the entrance into the data centers. The penetration testers nicely asked the friendly employees to allow them access to the data centers, and they did. The testers were then free to do anything on the servers. The employees need proper training.
The computer devices and the network do not have an antivirus installed. The social engineering attempt through baiting was successful because the computer devices of Sifers-Grayson were not protected. The computers did not have any form of anti-malware protection or were outdated. The firewalls were also not sufficient since they can be able to filter any malicious traffic from installed malware.
The computers at Sifers-Grayson do not have auto-run disabled. Auto-running media that are hostile devices can be used. A removable media containing malware left in a conspicuous place can infect host computers and the whole network. Due to the missing anti-malware software, attackers were able to compromise the PROM burner in DevOps labs. As a result, the malware compromised the AX10, the test vehicle being tested. During the trials, the malware made a cellular phone call to the Red Team, and they successfully took control of the test vehicle and landed it safely in a parking lot at Sifers-Grayson headquarters.
Cost of the Incident
Estimating the price tag of a widespread data breach can seem impossible. However, reviewing the data from a Data Breach Study 2016 can help establish some benchmarks. The report estimated an average breach to cost $7 million. The average costs were higher in 2011. The highest average cost per compromised record in 2016 was $221. In this case, the costs are directly spent on reducing the data breach consequences and assisting the victims. There are internal costs that are spent on the deal with the problem within the organization.
The direct costs to the organization are only 76 percent of the total costs. This includes the items such as investments in technology and legal fees. The greater portion of $145 is the data breach indirect costs. Included in this cost are the damage to the reputation of the organization and the increased customer churn rate. The data breach costs are higher in some organizations than others, such as technology, healthcare, service companies,s and life sciences. The heavily regulated industries, such as insurance companies, have higher average costs. Knowing these costs will help organizations ensure security for their organizations. Therefore, the total breach costs can be calculated as the number of compromised records multiplied by the average costs.
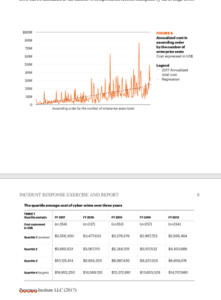
Ponemon Institute LLC (2017)
Business Impact of the Incident
Causes a drop in stock prices by an average of 5 percent in case of data breach disclosure. An organization has less likelihood of having a decline in stock prices if they implement strong security features. Sifers-Grayson does not have a proper security policy and, therefore, a slow response to data breaches. A report conducted on 113 companies shows that companies with poor security posture when a data breach occurs and do not respond experience a loss in stock for an average of 90 days (Centrify, 2017). The customers are also likely to switch to other producers.
The second impact on the business is on the brand reputation. This is perhaps the topmost impact of a breach which causes a loss of reputation and brand value. The breach on Sifers-Grayson would have the same impact. Chief Marketing Officers agree that brand value loss and diminishment is the highest security incident cost. The IT experts also assert that data breach is the greatest threat to their organization’s brand value and reputation. The problem is that most IT practitioners do not believe that the brand’s protection is their responsibility; this amounts to a staggering 71 percent of the experts (Centrify, 2017).
Another significant impact of a security incident is the impact on customer trust. Consumers expect organizations to be able to safeguard their personal information more than the companies assume. The customer’s expectations of security are even higher than that of the IT expert and CMOS. The customers may, however, have misplaced trust in certain industries.Sixty-eight8 percent of consumers have confidence that healthcare providers maintain their privacy for personal information protection. This contrasts sharply with only 26 percent of the customers trusting the credit card companies; financial organizations have merely 4.8 percent of customers trusting.
There may be other impacts of security impact on the business, for example, potential alignment costs and blind spots.Seventy0 percent of experts believe their companies have a low ability to contain breaches (Centrify, 2017). A potential blindspot may be the loss of stock price. There is a lot of worry regarding a company’s reputation loss following an incident. The IT function faces greater scrutiny after a data breach that leads to significant financial harm. Forty percent of IT professionals think this is the greatest impact.
Contract Requirement and Derivative
The contract requirements should follow the CFTC final rules adopted for cybersecurity testing. It is applicable to swap execution facilities, derivatives clearing organizations, swap data repositories, and designated contract markets (Cooley Alert, 2016). The contract will, therefore, require five security testing types:
- Security incident response plan testing
- Control testing
- Enterprise technology testing
- Penetration testing
- Vulnerability testing
Additionally, there will be a set minimum frequency of testing, use of contractors independent from the company, procedures for review, and internal reporting, which includes those for senior management. The contract will require an emphasis on security tests through board oversight and ongoing risk assessments. There must be an increased awareness of the vulnerabilities the company will face regarding cybersecurity. Additionally, the process should have a flexible risk-based approach that can be adapted to the company’s specific threats.
Similar Post: Cybersecurity System Security Report for Successful Acquisition
References
Cooley Alert. (2016). New Cybersecurity Rules for Financial Institutions. Retrieved from https://www.cooley.com/news/insight/2016/2016-10-11-new-cybersecurity-rules-for-financial-institutions
Centrify. (2017). THE IMPACT OF DATA BREACHES ON REPUTATION & SHARE VALUE. Retrieved from https://www.centrify.com/media/4772757/ponemon_data_breach_impact_study_uk.pdf
Khoussainov, R., & Patel, A. (2000). LAN security: problems and solutions for Ethernet networks. Computer Standards & Interfaces, 22(3), 191-202.
Ponemon Institute LLC. (2017). COST OF CYBER CRIME STUDY. INSIGHTS ON THE SECURITY INVESTMENTS THAT MAKE A DIFFERENCE. Retrieved from https://www.accenture.com/t20170926T072837Z__w__/us-en/_acnmedia/PDF-61/Accenture-2017-CostCyberCrimeStudy.pdf
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question
Final Project: Incident Response Exercise & Report
Your Task
You have been assigned to work on incident clean-up as part of the Sifers-Grayson Blue Team. Your task is to assist in analyzing and documenting the incident described below. The Blue Team has already created a set of enterprise architecture diagrams (see figures 1-4) to help with your analysis of the incident and preparation of the incident report as required by the company’s contracts with the federal government. After completing their penetration tests, the Red Team provided Sifers-Grayson executives with a diagram showing their analysis of the threat environment and potential weaknesses in the company’s security posture for the R&D DevOps Lab (see Figure 5).

Incident Response Exercise And Report
Your Deliverable
Complete and submit the Incident Report format. This file’s endless. Consult the “Notes to Students” for additional directions regarding completing the form.
Overview of the Incident
Sifers-Grayson hired a cybersecurity consulting firm to help it meet the security requirements of a contract with a federal agency. The consulting firm’s Red Team conducted a penetration test. It accessed the engineering center’s R&D servers by hacking into the enterprise network through an unprotected connection (see Figure 2). The Red Team proceeded to exfiltrate files from those servers and managed to steal 100% of the design documents and source code for the AX10 Drone System. The Red Team also reported that it had stolen passwords for 20% of the employee logins using keylogging software installed on USB keys left on the lunch table in the headquarters building employee lounge (see Figure 3). The Red Team also noted that the Sifers-Grayson employees were friendly and talkative as they opened the RFID-controlled doors for the “new folks” on the engineering staff (who were Red Teamers).
The Red Team continued its efforts to penetrate the enterprise. It used a stolen login to install malware over the network onto a workstation connected to a PROM burner in the R&D DevOps lab (See Figure 3). This malware made its way onto a PROM installed in an AX10-a test vehicle undergoing flight trials at the Sifers-Grayson test range (See Figures 1 and 4). The malware “phoned home” to the Red Team over a cellular connection to the R&D center. The Red Team took control of the test vehicle and flew it from the test range to a safe landing in the parking lot at Sifers-Grayson headquarters.
Background
Sifers-Grayson is a family-owned business headquartered in Grayson County, Kentucky, USA. The company’s address is 1555 Pine Knob Trail, Pine Knob, KY 42721. The president of the company is Ira John Sifers, III. He is the great-grandson of one of the company’s founders and the head of the engineering department. The chief operating officer is Michael Coles, Jr, Iraa John’sgreat-nepheww. Mary Beth Sifers is the chief financial officer and also serves as the head of personnel for the company.
Recent contracts with the Departments of Defense and Homeland Security have imposed additional security requirements upon the company and its R&D DevOps and SCADA labs operations. The company must comply with NIST Special Publication 800-171 Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations. The company must also comply with the Defense Federal Acquisition Regulations (DFARS)provisions, including section 252-204-701,2 Safeguarding Covered Defense Information and Cyber Incident Reporting. These requirements are designed to ensure that sensitive technical informatio provided by the federal government and stored on computer systems in the Sifers-Grayson R&D DevOps and SCADA lab is protected from unauthorized disclosure. This information includes software designs and source code. The contract requirements also mandate that Sifers-Grayson promptly report cyber incidents to the federal government.
SCADA Lab
The SCADA lab was originally set up in 1974. It has been upgraded and rehabbed several times since then. The most recent hardware and software upgrades were completed three years ago after the lab was hit with a ransomware attack that exploited several Windows XP vulnerabilities. The engineering and design workstations were then upgraded to Windows 8.1 Professional. A second successful ransomware attack occurred three months ago. The company paid the ransom in both cases because the lab did not have file backups that it could use to recover the damaged files (in the first case) and did not have system backups that it could use to rebuild the system hard drives (in the second case).
The SCADA Lab is locked into using Windows 8.1. The planned transition to Windows 10 is on indefinite hold due to technical problems encountered during previous attempts to modify required software applications to work under the new version of the operating system. This means that the lab’s incident response and recovery capability must support the Windows 8.1 operating system and its utilities.
R&D DevOps Lab
The R&D DevOps Lab was built in 2010 and is used to develop, integrate, test, support, and maintain software and firmware (software embedded in chips) for the company’s robots, drones, and non-SCADA industrial control systems product lines. The workstations in this lab are running Windows 10 and are configured to receive security updates per Microsoft’s monthly schedule.
Enterprise IT Operations
The company uses a combination of Windows 10 workstations and laptops as the foundation of its enterprise IT capabilities. The servers in the data center and the engineering R&D center are built upon Windows Server 2012.
Issues Summary:
- Newly won government contracts now require compliance with DFARS §252.204-7008, 7009, and 7012
- http://acq.osd.mil/dpap/dars/dfars/html/current/252204.htm
- http://acq.osd.mil/se/docs/DFARS-guide.pdf
- Derivative requirements include:
- Implementation of and compliance with NIST SP 800-171 Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations http://nist.gov/nistpubs/SpecialPublications/NIST.SP.800-171.pdf
- Compliance with DFARS 252.239-7009 Representation of Use of Cloud Computing and 7010 Cloud Computing Services (see http://acq.osd.mil/dpap/dars/dfars/html/current/252239.htm)
- Additional Contractual Requirements for Lab Operations include:
- Incident Response per NIST SP-800-61 (Computer Security Incident Handling Guide)
- SCADA Security per NIST SP 800-82 (Guide to Industrial Control Systems Security)
- Software / Systems Development Lifecycle (SDLC) Security per NIST SP 800-64 (Security Considerations in the System Development Life Cycle)
- Configuration Management per NIST SP 800-128 (Guide for Security-Focused Configuration Management of Information Systems)
Notes to Students:
- Your final deliverable should be professionally formatted and should not exceed ten pages. The goal is to be clear and concise in your reporting of your analysis of this incident.
- You may include annotated diagrams to illustrate your analysis and make your point(s). You may use the figures in this assignment as the foundation for diagrams in your final report (no citations required).
- Use the NIST Incident Handling Process (see Table 1) to guide your incident analysis.
- You may assume that the company has implemented one or more of the IT products you recommended in your Case Studies for this course. You may also assume that the company uses the incident response guidance documents you wrote for your labs and that the associated operating systems utilities are in use (e.g., you can assume that system backups are being made, etc.).
- DOCUMENT YOUR ASSUMPTIONS about people, processes, and technologies as if they were facts. Bu, don’t change any of the factual information provided in the incident report from the Red Team.
- Use the incident report form that appears at the end of this file. Copy it to a new MS Word document. After you perform your incident analysis, fill in the required information, attach the file to your assignment folder entry, and submit it for grading as your final project. Use your name for section 1 of the fore but provide useful but fictitious information for the remaining fields.
- For section 2 of the form, assign IP addresses in the following ranges to any servers, workstations, or network connections you need to discuss.
- R&D Center 10.10.150.0/24
- Test Range 10.10.148.0/24
- Corporate Headquarters 10.10.155.0/24
- For sections 2, 3, and 5, you should use and interpret the information provided in this file (Overview, Background, Issues Summary). You may use good creativity to fill in any missing information if necessary.
- For section 4 of the for,m, you may provide a fictitious cost estimate based upon $100 per hour for IT staff to perform “clean-up” activities. Reasonable estimates are probably in the range of 150 to 300person-hours. What’s important is that you document how you arrived at your cost estimate.
- Discuss the contract and derivative requirements for cybersecurity at Sifers-Grayson in 3 to 5 paragraphs under “Section 6 General Comments.”

