Creating a Java Application – Concurrency Concepts
Analysis of Appropriate Concurrency Concepts
Concurrency is the ability to execute multiple programs or sections of the program at the same time. It improves program efficiency and throughput since time-consuming tasks can be performed asynchronously (Silberschatz et al., 2019).
A modern computer contains several CPUs or cores within a single CPU. An application can use all cores for specific parts of the processing, finishing the work much faster as compared to sequential processing.
The basis of Java concurrency is threads. A thread is a lightweight independent sub-process.
Performance Issues With Concurrency
Concurrency is useful in maximizing hardware utilization; however, it has some drawbacks, especially if not implemented correctly. Some common threading issues include:
Blocking
A thread can block while waiting for another shared resource that is held by another thread. The program becomes increasingly unresponsive to user queries if the majority of the application server threads are consumed in a blocked state.
Deadlock
A deadlock can occur when a thread is waiting on a resource that is needed by another thread while the second thread is waiting on a resource that is required by the first lock (Silberschatz et al., 2019). This condition is called a deadlock since both threads are waiting on each other to release a lock, and this usually happens if the order of obtaining the locks is not planned appropriately.
Starvation
Starvation occurs when greedy threads make shared monitor(s) inaccessible for a long period of time (Mahafzah, 2014). For example, assume an object provides requests that take a long to return. If one thread calls this method frequently, other threads that also need the same frequent access to the object will often be blocked.
Race conditions
This occurs when the result is determined by which process out of numerous processes arrives at a point first (Mahafzah, 2014).
Vulnerabilities Exhibited with the Use of Strings
A string is an object that represents a sequence of character values. Strings are susceptible to the following vulnerabilities.
Connection String injection
Connection strings are a set of definitions that are used to link an application to a data source, e.g., MySQL database. For a connection string to occur, an attacker would need the following parameters: data source, initial catalog, user ID, and password (Meng et al., 2018). The attacker would then inject parameters into the connection strings using semicolons as separators, and as a result, they’ll end up gaining access by bypassing the normal authentication process without getting caught.
Sensitive data exposure
Sometimes, web applications do not properly protect sensitive data like credit card information or tax ids. A hacker might steal the information to perform crimes like credit card fraud, identity theft, etc (Cross, 2011). It is, therefore, advisable not to hardcode a salt value since once the code gets into production, an attacker can easily reverse hash values once they have the salt value.
Security of the Data Types Exhibited
Enhancing security in creating Java applications is equally important as making your application preformat, scalable and easy to maintain. Some measures include;
Use strong encryption and hashing algorithms
If the application has to store or transmit sensitive information, then one should be sure to implement a proper encryption technique (Meng et al., 2018). It is important to establish the type of encryption needed, for example, symmetric or asymmetric and how secure you need it to be.
Sanitize all inputs
Every user input is potentially malicious and should be validated accordingly. This is to help prevent untrusted data by all means. Cross-Site-Scripting (XSS) is a common security issue, which is basically the injection of a JavaScript code that is executed remotely. Therefore it is important to sanitize all the data before using it.
Avoid Serialization
Serialization transforms an object into a byte stream. It is also possible to de-serialize a byte stream to recreate the original object (Cross, 2011). Serialization is inherently secure because anyone can serialize your data to any file and read it even though you are not exposing any sensitive data in your classes. Instead, considering using a serialization format like JSON would be a good practice.
Difference between Java and C++ Versions
Java has built-in thread support with class thread, which can be inherited and override by the run method, while C++ does not have built-in thread support. It usually relies on third-party software.
Java implementation may be considered more secure than C++ because most exploits that involve Java are injection exploits such as cross-site scripting (XXS) and are not specific to the language itself, unlike C++.
Application Source Code
Below is the source code for the counter program. (see Appendix for screenshots and results)
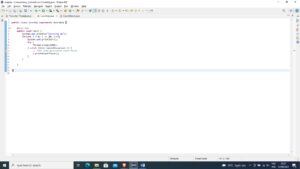
public class CountUp implements Runnable {
@Override
public void run() {
System.out.println(“Counting Up”);
for(int i = 0; i <= 20; i++){
System.out.println(+i);
try {
Thread.sleep(1000);
} catch (InterruptedException e) {
// TODO Auto-generated catch block
e.printStackTrace();
}
}
}
}
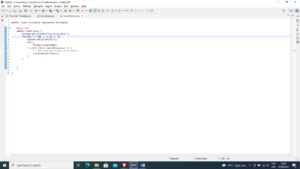
public class CountDown implements Runnable{
@Override
public void run() {
System.out.println(“Counting Down”);
for(int i = 20; i >= 0; i–){
System.out.println(+i);
try {
Thread.sleep(1000);
} catch (InterruptedException e) {
// TODO Auto-generated catch block
e.printStackTrace();
}
}
}
}
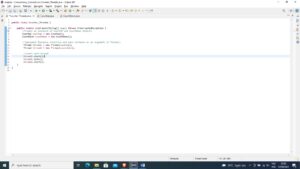
public class Counter_Threads {
public static void main(String[] args) throws InterruptedException {
//Create an instance of CountUP and CountDown objects
CountUp countup = new CountUp();
CountDown countdown = new CountDown();
//implement Runnable interface and pass instance as an argument to Thread()
Thread thread1 = new Thread(countup);
Thread thread2 = new Thread(countdown);
//start each thread
thread1.start();
thread1.join();
thread2.start();
}
}
References
Cross, M. (2011). Developer’s guide to web application security. Elsevier Science.
Mahafzah, B. (2014). Performance evaluation of parallel multithreaded A* heuristic search algorithm. Journal Of Information Science, 40(3), 363-375. https://doi.org/10.1177/0165551513519212
Meng, N., Nagy, S., Yao, D. (D., Zhuang, W., & Argoty, G. A. (2018). Secure coding practices in Java. Proceedings of the 40th International Conference on Software Engineering. https://doi.org/10.1145/3180155.3180201
Silberschatz, A., Galvin, P. B., & Gagne, G. (2019). Operating system concepts. J. Wiley & Sons.
Appendix
Program Execution Screenshots
Figure 1: CountUp Object
Figure 2: Count down the object
Figure 3: Main Class
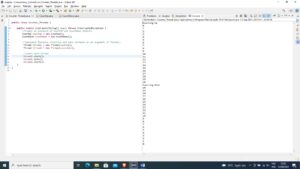
Figure 4: Results
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question
For your Portfolio Project, you will demonstrate an understanding of the various concepts discussed in each module. For the second part of your Portfolio Project, you will create a Java application that will exhibit concurrency concepts. Your application should create two threads that will act as counters. One thread should count up to 20. Once thread one reaches 20, then a second thread should be used to count down to 0. For your created code, please provide a detailed analysis of appropriate concepts that could impact your application. Specifically, please address:

Creating a Java Application – Concurrency Concepts
- Performance issues with concurrency
- Vulnerabilities exhibited with the use of strings
- Security of the data types exhibited.
Submit the following components:
- Word document with appropriate screenshots of your program execution, program analysis responses, and source code in the Word file.
- Submit your .java source code file(s). If more than 1 file, submit a zip file.
- Provide a detailed comparison between the performance implementations between the Java and C++ versions of your applications. Which implementation may be considered less vulnerable to security threats and why? Your detailed comparison should be 3-4 pages in length and should be formatted according to the APA formatting requirement.