System Scan Report
This report is a penetration testing report that involves scanning a system or operating systems for vulnerabilities. The host machine is a Linux operating machine hosted on a virtual machine. The target machine is a Metasploit operating system, which is also hosted in the virtual machine. The Metasploit operating system is a distro of Kali Linux, and its layout and tools look similar to those of Kali Linux. The virtual machine is connected to the internet to enable connectivity. Kali Linux tools for vulnerability scanning and assessment will be used, which include Zen map, open canvas, and open socket. The devices perform operations such as fingerprinting, port scanning vul, vulnerability assessment, and scoring. The main aim of this report is to highlight the procedures of conducting penetration testing and analyzing the results to harden systems by improving their security. This is the main goal of computer security.
Target
From the initial step, the following details were captured:
- Host IP address: 127.0.0.1
- Target IP address: 127.0.0.3
- Target operating system: Ubuntu
The system scanned in the target machine contains vulnerabilities and some open ports. Each tool displays different exposures, and thus, there is a need to combine means for proper scanning and testing.
Zenmap Scan
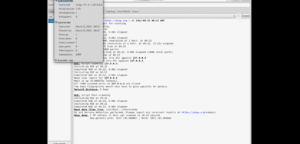
This is a Linux tool that prompts the user to the target IP address that ought to be scanned for vulnerabilities (Al Shebli & Beheshti, 2018). The IP address of the Metasploit machine is fed to the field. This tool scans for open ports and the services on those ports. After scanning, the tools revealed that the device had some open ports that could be used to get to the root of the device, namely port 5432, port 1524, and port 2049. Zen map is more of a command line, and thus, Nmap is invoked for a graphical interface. From a total of 1000 scanned ports, 2.1% were open and vulnerable, while the rest were closed. Other details revealed are the Mac address and the target machine’s operating system. The following picture shows the results after the deep scan.
OpenVAS Scan
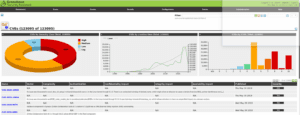
This is a vulnerability scanning tool in the Linux environment; it scans a machine for vulnerabilities and grades them as per their score (Al Shebli & Beheshti, 2018). The score is based on their impact, which can be high, low, or medium. The tool directed us to a third-party web service, namely Green Bone Security, which performed the scan and visualized the results in various formats. The results are displayed in the graphs shown in the diagram below. The tool also shows that some of the service running on the open port makes it more vulnerable and amount to a higher score than TLS and SSL services.
Open Socket
From the list of the open ports obtained from the port scanning process, the empty socket connection process tries to connect to the available port. From the target machine port, 8180 is tested for connectivity. Apache Tomcat is used for the empty socket connection, a third-party service (Khera, Kumar & Garg, 2019). This service is accessed by the web when invoked in the Metasploit tool. The following results were obtained.
Recommendations
From the results obtained in the penetration testing report, it is evident that the target machine, which is running a Linux operating system, has vulnerabilities. The vulnerabilities range from open ports to services and procedures in general. The vulnerabilities pose a threat to the organization as they can be exploited, which would cost the organization a lot (Khera, Kumar, & Garg, 2019). The scan comprises limited processes and tools, and thus, I recommend a more profound penetration process. After this has been done, all the vulnerabilities can be assessed and given a score. Based on this, mitigation activities to secure the system can then be implemented.
References
Al Shebli, H. M. Z., & Beheshti, B. D. (2018, May). A study on penetration testing process and tools. In 2018 IEEE Long Island Systems, Applications, and Technology Conference (LISAT) (pp. 1-7). IEEE.
Khera, Y., Kumar, D., & Garg, N. (2019, February). Analysis and Impact of Vulnerability Assessment and Penetration Testing. In 2019 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon) (pp. 525-530). IEEE.
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question
Describe an overview and discuss the scope of your network scan. Note the name of the operating system of your attack machine and discuss and describe the tools you will use (Zenmap, OpenVAS). Keep in mind that this report will be reviewed by nontechnical people who may not know about Zenmap or OpenVAS.

System Scan Report
Target
List the IP address and hostname of the target system as well as the IP address assigned to the attack machine. Focus on the open ports and describe the corresponding services associated with the open ports. Keep in mind that this report will be reviewed by nontechnical people who will not know about FTP or SSH or may not know what functions the services provide on a network. Put the information about the ports and corresponding services into a table and label it.
Zenmap Scan
Use Zenmap to scan the victim machine and include a screenshot of your connection to the victim system. Show a labeled screenshot of your Zenmap scan. Explain the results and how the client could be affected by any vulnerabilities that emerge.
OpenVAS Scan
Use OpenVAS to scan the victim machine and include a screenshot of your connection to the victim system. Show a labeled screenshot of your OpenVAS scan. Explain the results and how the client could be affected by any vulnerabilities that emerge.
Open Socket
You have already scanned the system with Zenmap and OpenVAS. Go back to either of the reports and look for a port that provided little information about the banner or provided you with an unknown. By manually connecting to the IP and port (socket), you can sometimes discover a vulnerability not listed by the tool. This shows the importance of not just relying on a device. Show a labeled screenshot of your connection to a socket that provided interesting results using a browser or Netcat, etc. If you find something concerning, explain that to the client.
Recommendations
Suggest that the client amend the contract to add a full penetration test. Explain that you are confident that you will be able to exploit the system and take proprietary data from the network.
References
Include at least two to three references in IEEE format.