Securing Data in the Cloud
1.0 INTRODUCTION
Belgine Limited, a Human Resources (HR) company, intends to move its HR applications and HR data into a community cloud. Having never used community cloud services before, Belgine Limited hired Stark Web Services, which is a cloud service provider, to provide them with a specific plan for migrating to and providing them with Software as a Service (SaaS) on the cloud. This report focuses on securing the data and applications of Belgine Limited in a cloud environment. An assumption made is that while Stark Web Services will provide security measures for Belgine Limited, the HR company will also implement some security measures on its end to increase the security of the data and applications.
2.0 PURPOSE
The implementation of a cloud solution for Belgine Limited will be conducted through a community cloud, which is shared with other clients. While shared tenancy with other clients might seem to present a security challenge for the data and applications of the company, it does not and ends up providing several benefits. Data and application replication on the cloud ensures that there is data availability when transmitting the data between the company and the cloud applications. Additionally, a community cloud provides increased flexibility and scalability while at the same time securing the data and applications. The adoption of community cloud services in Belgine Limited requires adherence to the General Data Protection Regulation (GDPR) and the Federal Risk and Authorization Management Program (FedRAMP). Adherence to the GDPR rules ensures that the company is not violating the guidelines provided by the European Union and that adherence to the FedRAMP guidelines ensures cloud services security is maintained using security measures defined by the National Institute of Standards and Technology (NIST).
3.0 PROJECT CONCEPTS
3.1 Development Life Cycles
Software development life cycle refers to the process involved in the development of an information system. This begins from the planning phase, through the analysis stage, the design stage, the development stage, and the implementation stage until the maintenance stage. The security development lifecycle refers to the process through which an information system is developed while taking into consideration the various security concerns that can arise and implementing measures to mitigate them. Both the software development life cycle and the security development life cycle address the development of an information system. A difference between the two is that security concerns in the system are addressed during the testing phase of the software development life cycle, while the security development life cycle aims at the development of information systems without any security concerns. Examples of SDLC models include the Agile model, the waterfall model, the V-Shaped model, the iterative model, and the spiral model. A recommendation is the use of the Agile model due to its ability to accept requirements changes at any development stage as well as its support for teamwork.
3.2 Architecture and Design Models
The waterfall model would require each stage of the migration process to the cloud HR application to be completed before another stage begins. The Agile model allows the migration process to be divided into smaller parts that allow different groups to work on the process at the same time. The extreme programming model allows adaptability during migration in case new requirements are defined. The spiral method allows the repetition of four phases until the migration process is completed.
| Architecture and Design Model | Pros | Cons |
| Waterfall Model | The expected outcomes after each stage are clearly defined. | It does not allow for additional requirements after the requirements stage is completed. |
| Agile Model | Allows new requirements to be defined during the migration process. | Accepts a lot of changes in the requirements, which can delay the migration process. |
| Extreme Programming | The migration process is guaranteed to be of high quality while adapting to the new changes defined during the process. | Similar to other models, too many changes can result in unexpected changes in the migration process. |
| Spiral Model | Additional requirements can be incorporated into the migration process. | Additional requirements might result in the migration process being never-ending or requiring more resources than intended. |
3.3 Threat Modeling Process
Threat modeling refers to the process where threats and vulnerabilities in an organization are identified, prioritized, and measures that can mitigate the identified threats and vulnerabilities are defined. Examples of threat modeling approaches include Microsoft threat modeling, which is part of the Microsoft Security Development Lifecycle (SDL), Microsoft’s Threat Analysis and Modeling (TAM), Practical Threat Analysis (PTA), and threat model framework and methodology for Personal Networks (PNs). (Amini et al., 2015)
3.4 Other Considerations
Some of the considerations that are useful for data protection include various data access policies, data encryption, tokenization, and the use of two-factor authentication.
4.0 PROJECT DEFINITION AND SCOPE
4.1 Belgine Limited HR Company Characteristics
Belgine Limited provides various Human Resource capabilities to its clients. The company intends to move its HR data and HR applications to a cloud service in an effort to increase the productivity and efficiency of the company. By moving the data and application to the cloud, the organization will not only increase flexibility in the company but also increase scalability, which in turn contributes towards the increased productivity and efficiency of the company. Some of the security characteristics of the current HR applications include the use of access control to authenticate the users of the applications. Additionally, some features in the applications are limited to some of the users.
4.2 Cloud Options
Various organizations provide cloud services. Some cloud services available to the organization include Amazon Web Services, Microsoft Azure, Google Cloud, IBM Cloud, Oracle Cloud, MapR, and Cloudera. The proposed cloud service for Belgine Limited is Amazon Web Services. Apart from being highly customizable, Amazon Web Services also offers a secure cloud platform. Therefore, it best fits the requirements of Belgine Limited for moving the HR applications and HR data to the cloud.
The high-level architecture of Hadoop consists of the MapReduce layer and Hadoop Distributed File System (HDFS) layer. JobTracker constitutes the Master Node in the MapReduce layer, while the NameNode makes up the Master Node in the HDFS layer. Amazon Web Services offers various services in relation to Infrastructure as a Service (IaaS) and Platform as a Service (PaaS). Examples include VMware Cloud, AWS Migration Acceleration Program (MAP), and various migration tools. The architecture of the AWS cloud environment includes application, management, service, storage, and security.
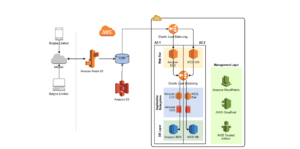
Securing Data in the Cloud
4.3 Functional and Security Architecture
Cloud computing architecture requires the implementation of cloud security architecture to provide security measures for the data and applications in the cloud. One of the security measures is the implementation of data backups. Data backups ensure that data can be recovered in case of an attack. Another security measure is the implementation of virtual firewalls that prevent unauthorized access to the data at rest and in use. Additionally, tokenization and certificate-based authorization can secure data at rest and in use. Similarly, using access control and authentication can also be used to secure the data (Zissis and Lekkas, 2012). Data in transit can be secured through encryption, while the implementation of monitoring tools can identify malicious traffic between Belgine Limited and the cloud services implemented (Kuyoro et al., 2011).
4.4 Specific Scope
Different measures can be implemented to secure the data in transit once Belgine Limited implements the Amazon Web Services cloud services. Examples include encryption and authentication of the data as well as the implementation of updated security standards. Once the data in transit has been encrypted, secure encryption keys and certificate storage is recommended. This can be achieved using the Amazon Web Services Certificate Manager. Monitoring tools can be implemented to identify unauthorized access to the data before it reaches its destination. Securing data in transit can also be achieved through authentication of the communications between Belgine Limited and AWS. Protocols such as Transport Layer Security (TLS) and IPsec can be used to authenticate the communication. Implementing such measures prevents man-in-the-middle attacks and data leaks, which would lead to loss of data confidentiality and integrity.
5.0 FUNCTIONAL ANALYSIS
5.1 Methodology
System Quality Requirements Engineering (SQUARE) refers to the process involved in the definition of the security measures for information systems and the applications in the systems. The SQUARE steps include identifying the assets and the security goals, defining measures to secure the data, performing the risk assessment, prioritizing the security requirements, and analyzing the prioritized security requirements (Mead and Stehney, 2005).
5.2 Ways for Securing Data in the Hadoop Cloud Environment
Securing data in the Hadoop cloud environment involves the implementation of various security measures. An example is the encryption of the data in transit, as well as securing the communications using protocols such as TLS, SSL, and IPSec. Proper key management of the encryption keys used to secure the data in transit. Making sure that unauthorized individuals do not access the data stored in Hadoop can be achieved by using various authentication protocols (Olavsrud, 2012).
5.3 Technology Evaluation
Access control in the company can be implemented in various models. Access control determines the individuals at Belgine Limited who access the specified resources in the cloud. Some of the access control models that Belgine Limited can implement in the cloud services include role-based access control, mandatory access control, attribute-based access control, and discretionary access control.
6.0 SYSTEM DESIGN
The components of the data-in-transit protection model include encryption techniques, key management systems, and secure connection protocols. Some of the encryption techniques used in securing the data in transit include Advanced Encryption Standard (AES), RSA, and Triple Data Encryption Standard (TripleDES). Key management is used to manage the encryption keys used to secure the data in transit. Some of the secure connection protocols include Transport Layer Security (TLS), Secure Shell (SSH), and HTTPS.
7.0 LIFE CYCLE PLANS
7.1 Software Development Plan
The agile methodology is the software development plan chosen for the migration of HR data and HR applications to the cloud. The various phases included in the model include the analysis stage, the design phase, the development phase, the testing and implementation phase, and maintenance.
7.2 Testing and Integration
Testing includes analyzing the quality of the Software developed, while integration includes the execution of the Software developed. Implementation testing analyzes whether the Software’s various functions work correctly to ensure the data’s security in transit. Integration testing analyzes whether the functionalities of the system effectively function together with other functionalities.
7.3 Deployment
Security in cloud computing can be implemented in various areas of cloud architecture. An example is the implementation of access control measures and authentication protocols on the Infrastructure owned by Belgine Limited. The organization can also implement physical security measures to protect the company’s networking components. Security measures can also be implemented in the cloud by AWS. Data encryption can be used to secure the data in transit.
7.4 Operation and Maintenance
After the implementation of the HR application and HR data in AWS, the cloud services must be maintained to ensure that they are operating effectively. The implementation of a monitoring tool checks whether the data in transit is compromised. Additionally, the monitoring tool can be used to identify whether the encryption measures implemented are correctly functioning.
7.5 Disposal Plan
Once Belgine Limited no longer requires the use of cloud services, it will take different measures to ensure the security of the organization’s data. The initial data sanitization process includes defining service level agreements (SLA) with AWS. The SLA details the various stages to undertake once the organization decides to conduct data sanitization. Standardization of the stages to take place during the data sanitization is then defined. A chain of custody should also be maintained during the data sanitization process to ensure that unauthorized individuals do not access confidential data.
8.0 CONCLUSION
The HR applications and data migration to the cloud will be implemented on Amazon Web Services. To achieve this, Belgine Limited will use the agile migration methodology. The migration process will require Belgine Limited to take into consideration various security measures to ensure that cyber-attacks do not occur in the company. Examples of security measures include data encryption and access control to protect the data in transit, data at rest, and data in use.
References
Amini, A., Jamil, N., Ahmad, A. R., & Zaba, M. R. (2015). Threat modeling approaches for securing cloud computing. Journal of Applied Sciences, 15(7), 953-967.
Huang, J. (2019, January 17). Automating Your AWS Landing Zone Deployment to Speed Up Large-Scale Migrations. Retrieved February 12, 2020, from https://aws.amazon.com/blogs/apn/automating-your-aws-landing-zone-deployment-to-speed-up-large-scale-migrations/
Kuyoro, S. O., Ibikunle, F., & Awodele, O. (2011). Cloud computing security issues and challenges. International Journal of Computer Networks (IJCN), 3(5), 247-255.
Mead, N. R., & Stehney, T. (2005). Security quality requirements engineering (SQUARE) methodology. ACM SIGSOFT Software Engineering Notes, 30(4), 1-7.
Olavsrud, T. (2012, November 8). How to Secure Big Data in Hadoop. Retrieved February 12, 2020, from https://www.cio.com/article/2390490/how-to-secure-big-data-in-hadoop.html
Vines, R. L. K. R. D., & Krutz, R. L. (2010). Cloud security: A comprehensive guide to secure cloud computing (pp. 35-41). Wiley Publishing, Inc.
Zissis, D., & Lekkas, D. (2012). Addressing cloud computing security issues. Future Generation computer systems, 28(3), 583-592.
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question 
Project 4 instructions
Project 4 brings us to a business sector enterprise concerned about its Human Resources (HR) capabilities. The HR function has its own confidential and sensitive information, just as finance and medical have theirs. The fictitious company you choose in this project wants to move its HR applications and HR data into a community cloud, sharing tenancy with other clients. It has not used the cloud before. Note that community cloud means something very specific. Be sure you are writing about this type of cloud solution and since the enterprise wants to move its HR application to the cloud, the solution is looking for Software as a Service (SaaS) on the community cloud.

Securing Data in the Cloud
For this project, you are:
- a member of a team within the community cloud service provider. You are NOT at the enterprise which is wanting to move its HR.
- one of several security software architects on the team
- assigned to the project to provide the HR company with a plan for migrating and providing the HR company Software as a Service (SaaS) on the cloud.
Specifically, you are to:
- Deliver a Software Development Life Cycle (SDLC) driven report for securing data and applications in a community cloud environment.
The enterprise should gain enough specific information from you, about the solution you are offering, to be able to make the decision to use your cloud services.
This project is distinguished from your past projects by its emphasis on the cloud solution and SDLC. Please avoid being so generic that these attributes are inconsequential to what you provide.
Step 4: Provide Analysis and Planning for Evaluating Technologies
Once the team members have understood ways to secure data in the cloud, the team will analyze and develop a plan to use technologies and/or techniques to meet the functional requirements developed earlier for protecting client data protection in transit.
To prepare, click the following links and learn more about virtualization and cloud computing:
To be completed by a designated team member:
Compare different technologies and techniques, including encryption, access control, and other techniques. Consider their efficiency, effectiveness, and other factors that may affect the security of the data in the cloud. Include your reasoning and conclusions in your evaluation. Conclude which techniques are generally better and stronger and provide your reasoning.
You will include this summary in your report.
Access control
Access control is the process by which permissions are granted for given resources. Access control can be physical (e.g., locked doors accessed using various control methods) or logical (e.g., electronic keys or credentials). There are several access control models, to include:
- Role-based access control: Access is granted based on individual roles.
- Mandatory access control: Access is granted by comparing data sensitivity levels with user sensitivity access permissions.
- Attribute-based access control: Access is granted based on assigned attributes.
- Discretionary access control: Access is granted based on the identity and/or group membership of the user.
The access control model used is determined based on the needs of the organization. To determine the best model, a risk assessment should be performed to determine what threats might be applicable. This information is then used to assess which model can best protect against the threats.
- Cloud to Device Messaging
To navigate the tab controls use the arrow keys. Use the Tab key to move to the tabs content.
As cloud computing continues to expand its reach to new platforms, service providers are increasingly offering cloud-on-mobile or mobile cloud computing to manage and operate mobile applications.
The first iteration of mobile cloud computing has come in the form of mobile Gmail and Google Maps, which carry out data storage and processing activities on mobile devices, not necessarily on the cloud.
The next generation of mobile cloud computing, such as Android 2.2’s “Cloud to Device Messaging (C2DM)” feature, conducts data storage and processing outside the mobile device, on the cloud. One example of this is the “Chrome to Phone” app.
Benefits
- Web-developed applications, requiring only one version, will run on servers rather than on-site, and handset requirements will be automatically minimized and simplified.
- Mobile devices will become more powerful when their memory is freed, as data storage and processing will be offloaded to the cloud.
- Organizations will benefit from data-sharing applications and enhanced collaboration. Individual users will discover that remote-access applications enable them to monitor their PCs, DVRs, and home security systems.
Barriers
- Mobile Web connectivity is inconsistent in some areas. This can be addressed with technologies like HTML5, which uses local caching to help mobile cloud applications transmit at faster speeds.
- All platforms (physical, virtual, and mobile) connected to the cloud need to be secured. However, keeping in mind the limited storage of mobile devices, these security technologies must run on the cloud without adversely affecting device performance, battery life, or processing resources.