Investigation Project Plan
Disclaimer
The circumstances used in this investigation project plan are for academic purposes. Should there be any similarities in the case scenario used with real litigation cases, they should be considered highly coincidental with no relation to actual court cases. All product information in the cases described below does not serve advertisement purposes. Information used in this document should, therefore, strictly be considered for learning purposes only.
Do you need an authentic “Investigation Project Plan research paper” copy? Reach out to us.
Table of Contents
Principles and Procedures followed. 5
Guidelines as per NIJ recommendation. 5
Procedure and Policy Development 5
Checklist of Forensic Equipment and Software. 12
Recovery of deleted partitions. 12
Password recovery and data decryption. 12
Interview forms with questions. 18
Questions for the Prosecution and lead detectives. 18
Questions for the lead Detectives and associated law enforcement colleagues. 19
Questions for Information Technology Administrators. 19
Questions for the suspect and victim’s company security personnel / Witnesses. 19
Questions for the Prosecution. 20
Questions for the digital forensic investigation team.. 21
Equipment and software cost 24
Labour and Other miscellaneous expenses. 25
Appendix A – Application for a Search Warrant 29
Appendix C- Search and Seizure form. 30
Appendix D – Chain of Custody. 32
Appendix E– Sample Removable Media Worksheet 33
Appendix F – Hard drive Evidence Worksheet Sample. 34
Abstract
The purpose of the investigation project plan described below is due to an official request granting the authority to offer assistance in conducting a digital forensics investigation of two computers and a thumb drive. Producing a thorough investigation project plan will be challenging before meeting lead detectives and the prosecutor. Therefore, this investigation project plan is designed to identify key people and activities, possible criminal activity to be evaluated, investigation timeline, and people of interest. All human, time, and equipment resources are required to complete the investigation. The digital forensic process will primarily entail collecting information, examining, analyzing, and documenting findings in a report. In this case, the investigation project plan will detail the forms and documents required to obtain legal, criminal, and technical data while preserving the integrity of the information. The examination will comprise the forensic processing of information manually or with the help of digital software and evaluating information of interest without tampering with data integrity. Legal analysis methods proposed will be used to inspect collected data to facilitate the extraction of significant information concerning the suspected criminal activities and the parties involved. A conclusion of the proposed actions, selected procedures and tools, and recommendations for various aspects of the investigation process will be discussed.
Keywords: investigation project plan, digital forensics
Abbreviations
NIJ – National Institute of Justice
SWGDE – Scientific Working Group on Digital Evidence
WIFI – Wireless Fidelity, for internet connection
SSID – Name of a wireless network
TB – Terabyte
IT – Information Technology
Principles and Procedures Followed
All actions in the subsequent sections shall conform to the following principles and procedures. These guidelines are standard industry practices proposed by SWGDE and NIJ.
General Principles
- All actions shall not alter data integrity.
- Investigators must be competent enough to obtain original data of interest.
- Audit trails must be made.
- Investigators must adhere to ethical and legal guidelines.
Guidelines as per NIJ recommendation
Procedure and Policy Development
The following procedures must be met:
- The integrity of digital evidence must be preserved.
- Legal policies that govern the reception, analysis, and handling of evidence must be adhered to.
- Required forms, a list of contacts, and evidence acceptance criteria should be considered.
- Competent examiners will be prioritized during examination assignments.
Assessment
- There will be consultation with the case detectives and Prosecution.
- Company premises and personnel will be consulted.
- All required forms will be completed and submitted.
Acquisition
- Since digital evidence is fragile and prone to change or damage, copies of the original data will be copied to hard drives to maintain the original data integrity.
- Chain of Custody and Search and seizure forms will be used to acquire evidence and indicate physical evidence handlers.
Examination
This process is intended to obtain and analyze digital information. Obtaining data will be from laptop hard drive media, whereas analysis covers the scope of interpretation and conversion of recovered data into a format that makes sense.
Reporting
All actions and procedures must be appropriately documented with a sound recommendation of the investigation findings.
Storage
Evidence will be stored in a locker room accessible by fingerprint biometric scan entrances. Security footage will also be live in the storage facility. To acquire evidence, one should have proper documentation.
Meetings and Agendas
This section will highlight meetings and their objectives among various groups. Each meeting facilitates building informative decisions toward evidence analysis and the final recommendation upon finishing the investigation. According to Schwartz (2015), as detailed in the table below, various meeting categories have specific groups attending the meeting, the meeting’s objectives, a schedule, frequency of meeting, and an estimated duration per meeting.
Table 1
| Meeting Category | Group | Objective | Schedule | Frequency of meetings/ week | Duration
(hours) |
| 1. a | Lead detectives, the digital forensic investigation team, and the Prosecution | Crime background definition.
Creation of a list of contacts and identification of Participants. |
Week 1 | 1 | 2 |
| b. | Lead detectives, the digital forensic investigation team, and the Prosecution | Updates on investigation status.
|
Week 1-4 | At least once or per arising need to meet. | 2 |
| 2 | Lead detectives
and The Digital forensic investigation team |
Evidence inventory | Week 1 | At least thrice/ depending on the need for clarification by the investigation team. | 4 |
| 3 | Witnesses | Establish a foundation for behavioural evidence data collection.
Gathering facts about the incident, the suspect’s motive, and victimization or harm. |
Week 2-3 | per arising need for clarification | 3 |
| 4 | Company’s IT Management for suspect | Provision of data essential to analysing data of interest in the investigation.
Timeframe analysis. Assessment of activity logs |
Week 2-3 | At least thrice/ per arising need for clarification | 3 |
| 5 | Company’s security team | Assessment of suspect’s physical and behavioural activities.
|
Week 2-3 | At least twice/ per arising need for clarification | 2 |
| 6 | Coworkers | Crime scene Assessment.
Suspect’s behavioural and motive data collection.
|
Week 2-3 | At least twice/ per arising need for clarification | 2 |
| 7. | Digital Forensic Investigation Team | Identification of team and roles.
Scheduling of activities. Creation of interview questions. Budget design and proposal. |
Week 1
|
5 | 4 |
| b | Data collection | Week 2 | 5 | 3 | |
| c | Data examination and analysis | Week 3 | 5 | 4 | |
| 8 | Digital Forensic Investigation Team, lead detectives, and the Prosecution | Discussion on findings and recommendations.
Reporting and Court Presentation |
Week 4 | 5 | 5/as demanded by the Prosecution and law enforcement. |
List of Contact People
The following is a list of key contact people who are significant in making the research successful. They include:
- Forensic examiners
- Lead detectives from local law enforcement
- Case prosecutor
- Coworkers
- The suspect’s company’s security personnel
- Witnesses
- The company’s information technology management
Required forms
Application for Search Warrants: According to the United States courts, an “Application for a search warrant” (2010) refers to a legal court order document that requests a search warrant used by local enforcement.
Chain of Custody Form: It documents who handled what physical evidence during the digital forensic investigation.
Consent Form: This form will facilitate the accessibility of digital evidence from suspects, witnesses, or victims. Without the correct language, the evidence presented to the court may not stand (Magnet Forensics – “Consent to Search,” 2020).
Search Warrant: This a document issued by a judge or magistrate to authorize law enforcers to search vehicles, locations, or people for evidence.
Removal Media Worksheet: This document records comprehensive data about removable media from a computer device. In this case, the thumb drive will be of focus.
Hard Drive Evidence Worksheets: This refers to a document that records comprehensive data about hard disk drives.
Proposed Keyword Searches – According to Billingsley (2016), this tool will be able to identify data of interest from a given data set.
Checklist of Forensic Equipment and Software
This section details significant equipment and software required during the digital forensic investigation. Week 1 meetings revealed that the computers are Windows-based laptops. These include:
Recovery of deleted partitions
EaseUS data recovery software
Password recovery and data decryption
EPRB
RAM analysis
WindowsScope
Storage Unit
Fingerprint biometric storage locker
Personal equipment
Power supplies
Forensic laptops
USB and network cables
Blank hard drives – 1 TB storage space
Investigative process
- The law enforcement officers applied for a search warrant.
- A United States judge issued the search warrant to enable the search for evidence.
- Law enforcement officers confiscated two laptops and a thumb drive.
- Forensic examiners made directories to store evidence files on their external hard drives.
Table 2
Evidence Inventory
| Item No | Item | Owner abbreviation | Operating System | Assessment Tool |
| 1 | Acer Aspire| V5 Laptop | P. W | Windows 10 Pro | WindowScope
EaseUS |
| 2 | Lenovo ThinkPad SL510 Laptop | P. W | Windows 10 Home | WindowScope
EaseUS |
| 3 | USB Thumb Drive | P. W | – | EaseUS
EPRB |
Image 1
Deleted screenshots were recovered by EaseUS software.
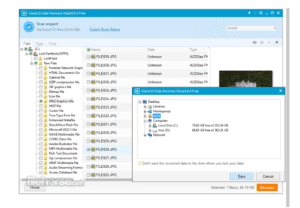
EaseUS data recovery Image
Note. EaseUS data recovery Image (EaseUS, 2020)
Table 3
The logical data extraction was done on the two laptops and thumb drives.
| Process ID | Item | Objective | Significance to case |
| 1 | Unallocated space | Facilitate recovery of deleted files | Enable recovery of messages and images related to financial fraud. |
| 2 | Pertinent information | Location of data of interest using file content, file’s location on the drive, file headers, and extensions. | Locate files and images related to the impersonation of financial administrators.
Observation of BIOS data and other timeframe information. |
| 3 | File system | Facilitate revelation of file size, time stamps, file names, attributes, and directory structure. | Two different operating file systems were extracted. |
Analysis
Forensic examiners validated the accuracy of BIOS time and date before proceeding with timeframe analysis. Information that was extracted detailed:
- Paul Walker’s time and day of the created screenshots on critical financial accounts.
- Messages found coincided with those sent from Paul’s Acer laptop.
- There were deleted plans on how to implement the financial fraud plan.
- On the day of the suspected criminal activity, BIOS data revealed the duration of his implementation plan.
Data encryption
- Files were evaluated for metadata related to financial fraud.
- The type of operating system was examined.
- Files were analyzed for data related to encryption programs.
- User configuration settings were analyzed to identify default storage paths.
- Examination of the devices revealed that the thumb drive containing embezzled account information was hashed using the MD5 algorithm.
Image 2
Recovered Account data
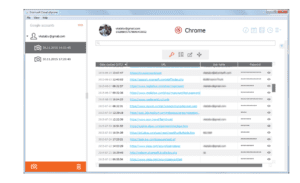
Image 2
Elcomsoft’s EPRB recovered account information (Elcomsoft, 2020)
Interview forms with questions
People involved with answering these questions entail the Prosecution, coworkers, company security and management, and lead detectives. Essential questions that will help with this investigation include the following:
Questions for the Prosecution and lead detectives
- What is the expected time frame for collecting, examining, analyzing, and reporting findings concerning the evidence, respectively?
- Are there any other aspects of the investigation not clarified in the police reports?
- Have other investigators been hired to investigate the same case?
- What aspect of the case are they inspecting?
- What are the investigator’s contacts?
- Have any witnesses come forward?
- Is law enforcement aware of any accomplices?
- What possible evidence implied the motive to commit the crime?
- Was any digital equipment logged into police evidence?
- Is there any legal document to support the confiscation of the devices?
- How were the two computers and a thumb drive obtained? Was volatile data at the time of acquisition affected?
- Was the chain of Custody clarified to other investigators, if any?
Questions for the lead Detectives and associated law enforcement colleagues
- Who are the lead detectives for the case?
- What offence or crime is being investigated?
- What were the critical offender characteristics reported?
- Were the crime scene’s characteristics defined?
- How was the evidence catalogued?
Questions for Information Technology Administrators
- What is the description of the computers and thumb drive?
- What can network traffic data be obtained from the suspects’ computers?
- Did computers have an operating system? If yes, which Operating system was running, and what is the file system type for the three devices?
- Did the devices have internet access? Were they connected to the company’s network?
- What was the WIFI SSID used?
Questions for the suspect and victim’s company security personnel / Witnesses
- Does the suspect’s company have CCTV footage?
- Can the system’s footage account for the suspect’s whereabouts when the crime was committed?
- Is the victim captured in the security video?
- When did the alleged offender and the victim enter and exit the work premises?
- Are there complaints filed against the suspect?
- Who saw the suspect do suspicious activities?
- What steps did they make to stop the suspect?
- What was the response from the security team?
Questions for coworkers
- How is the suspect’s work relationship with colleagues?
- How is the victim’s work relationship with colleagues?
- Is the suspect aggressive or friendly?
- Does the suspect have issues with company management?
- How does the suspect feel about their financial status?
Questions for the Prosecution
- Who is the prosecutor?
- Are there any suspects in Custody?
- Who are the primary suspects?
- Are there legal issues about the admissibility of evidence that should be addressed?
- How did law enforcement authenticate evidence?
- What could potential defence strategies be used against the case?
- Where will the evidence be processed during the investigation?
Questions for the digital forensic investigation team
This set of questions will highlight the investigation team’s competence and critical aspects that law enforcement may have left out yet are critical to in identifying incriminating evidence.
- What methods will be used to extract data of interest?
- How will the data be analyzed? Did the suspect alter the computer’s timeframe or encrypt data on the drives?
- What will typical file and application analysis techniques be used?
- How will evidence ownership analysis and processing be conducted?
- Was there any deleted data?
- What does evidence analysis reveal about the victim?
- Was the victim harmed in any way due to the suspected cybercrime?
- What findings have been uncovered from evidence analysis?
- What can legal and unbiased recommendations be given?
Investigation Timeline
Image 3 – investigation timeline process flow

Image 3
Week 1
The Lead detectives, the digital forensic investigation team, and the Prosecution will meet once for two hours to define background information. During the session, participants will be identified, including other detectives making it clear to generate a list of contact people.
The digital forensics investigation team shall identify team members and their roles, schedule activities, create interview questions, design a budget, and establish policies to guide the investigation process. The team will meet at least five times weekly, four hours per meeting.
Week 1- 4
The lead detectives, the digital forensic investigation team, and the Prosecution will meet at least thrice a week for 2 hours to share updates on the status of the investigation.
Week 2-3
The Digital Forensic Investigation Team will collect data and devices suspected to hold evidence. In liaison with various groups such as witnesses, coworkers, security personnel, and IT management, the investigation team will establish a foundation for behavioural evidence data collection, gather facts about the incident, the suspect’s motive and victimization or harm, assess and provide data that is essential to the analysis of data of interest in the investigation, bios timeframe, activity logs, suspect’s physical and behavioural activities, and motive.
Week 3
The Digital Forensic Investigation Team will examine data and its analysis for five sessions, each five hours long.
Week 4
The Digital Forensic Investigation Team, lead detectives, and the Prosecution will finally meet at least five times for five hours per meeting to discuss findings and recommendations and prepare for court presentations.
Investigative Budget
The hourly rate for forensic investigators is derived from salary.com, “hourly rates for digital forensic investigators” (2018). Retail product prices were obtained from Amazon.com, whereas cyber-forensic software and equipment costs were obtained from individual product websites such as WindowScope Products (2020) and Elcomsoft (2020).
Table 4
Equipment and software cost
| Item | Quantity | Rate | Sub-Total |
| Blank hard drives – 1 TB storage space
|
3 | $48 | $144 |
| USB cables
|
2 | $10 | $20 |
| Forensic laptops
|
3 | 400 | $1200 |
| Power supplies
|
2 | $135 | $270 |
| WindowsScope
|
1 | $7,699 | $7,699 |
| EPRB
|
1 | $2000 | $2000 |
| EaseUS data recovery software
|
3 | $70 /month | $210 |
| Write blocker | 1 | $399 | $399 |
| Total | $11,942 |
Table 5
Labour and Other miscellaneous expenses
| Forensic Examiners | 2
Minimum Total Expected working hours = 80 |
$32/hour | $5,120 |
| Miscellaneous Expenses | $350 | $350 | |
| Total | $5,470 | ||
| Total Investigation budget | $17,412 |
Conclusions
The investigation project plan adhered to principles recommended by NIJ from the collection of evidence to final processing. The purpose of the investigation plan was to assist in investigating two laptop computers and a thumb drive to locate evidence that implicated the suspect, Paul Walker. After a thorough evidence examination and analysis, it was clear that Paul had embezzled company funds, encrypted the thumb drive containing incriminating evidence, and deleted related data on his two home and office laptops and the thumb drive. Therefore, the digital forensic investigation team recommends presenting these findings to the lead detectives and case prosecutors for court processing.
References
Amazon.com: digital forensic software. (2020). Retrieved 17 July 2020, from https://www.amazon.com/s?k=digital+forensic+software&crid=3A2SFS726BPWP&sprefix=digital+forensic+soft%2Caps%2C448&ref=nb_sb_ss_i_1_21
Billingsley, J. (2016). Beyond Keywords: Is Keyword Search Becoming Obsolete In The New Age Of Forensic Digital Investigation? – Forensic Focus. Retrieved 17 July 2020, from https://www.forensicfocus.com/articles/beyond-keywords-is-keyword-search-becoming-obsolete-in-the-new-age-of-forensic-digital-investigation/
Consent to Search Form – Magnet Forensics. (2020). Retrieved 17 July 2020, from https://www.magnetforensics.com/consent-to-search-form/
Elcomsoft Desktop Forensic Bundle | Elcomsoft Co.Ltd. (2020). Retrieved 17 July 2020, from https://www.elcomsoft.com/edfb.html
Elcomsoft EPRB data recovery. (2020). Retrieved 17 July 2020, from https://www1.elcomsoft.com/ecx.html
The hourly wage for Digital Forensic Investigator | Salary.com. (2020). Retrieved 17 July 2020, from https://www.salary.com/research/salary/posting/digital-forensic-investigator-hourly-wages
Recommended Forensic Practices. Retrieved 17 July 2020, from https://us-cert.cisa.gov/sites/default/files/recommended_practices/Forensics_RP.pdf
Schwarz, R. (2015). How to Design an Agenda for an Effective Meeting. Retrieved 17 July 2020, from https://hbr.org/2015/03/how-to-design-an-agenda-for-an-effective-meeting
What is Digital Forensics? History, Process, Types, Challenges. (2020). Retrieved 17 July 2020, from https://www.guru99.com/digital-forensics.html
WindowsSCOPE Cyber Forensics 3.2 – WindowsSCOPE. (2020). Retrieved 17 July 2020, from http://www.windowsscope.com/product/windowsscope-cyber-forensics-trial/
Appendices
Appendix A – Application for a Search Warrant
Image – Application of Search Warrant (United States courts- Search Warrant, n.d.)
Appendix C- Search and Seizure form.
Appendix D – Chain of Custody
Evidence Chain of Custody form
Case Number: Offense:
Submitting Officer:
Victim:
Suspect:
Time and date seized: Location of confiscation
| Item | Quantity | Evidence Description |
| Item | Time/Date | Chain of Custody
Released by |
Received by |
Comments |
Appendix E– Sample Removable Media Worksheet
Appendix F – Hard drive Evidence Worksheet Sample
Similar Post: Telematic devices in health insurance companies
ORDER A PLAGIARISM-FREE PAPER HERE
We’ll write everything from scratch
Question 
Guidelines for Investigation Project Plan
Your report must be organized and written in a way that is easy to follow. Include all requirements that are identified in the Project 1 steps as well as here in the guidelines.

Investigation Project Plan
Each section of the report should be identified. Use the terms figure and table to refer to all images and graphics. Take time to check your sentence structure, expression of ideas, and spelling. Your writing must flow and make sense.
Tables, screenshots, graphs, and artifact images in your report should be individually labelled and numbered using APA format (e.g., Table 1 Expense Budget, Figure 1 Screenshot of Washer ATM Image). Check the UMGC library for the proper APA formatting.
Your instructor may require additional details and different formatting approaches. Rely on your instructor’s guidance and feedback to produce the highest deliverables to meet or exceed performance standards for Project 1 in DFC 620/CST 640.
Consider the following sections as the minimum starting point. Be sure to click each tab for more information.
- Title Page Include the title, your name, course name, and date.
- Table of Contents This will be a list of all upcoming sections.
Purpose In brief, this section should include what you, as the investigator, are trying to achieve through this investigation.
Note: You may want to include an abstract since you will be required to include an abstract in many of the future papers you write in the UMGC graduate program. Your instructors expect it, and your paper submissions will stand out as polished graduate-level work. If you don’t know an “abstract”, review it in the UMGC library or search online. This is the time to learn and grow.
Meetings and Agendas Identify the types of meetings that should be held and the issues to be discussed with each group of meetings that need to be conducted. Be sure to include in the timeline section when the meetings should occur.
Create a meeting agenda to accompany each proposed category of meetings. (You can research how to prepare a proper agenda format). Your instructor may provide feedback on this issue.
- Required Forms Application for Search Warrants
- Chain of Custody Form – Completed
- Consent Form – Example
- Search Warrant – Example
- Removal Media Worksheet
- Hard Drive Evidence Worksheets
- Proposed Keyword Searches
- Forensic Equipment and Software Checklist lists everything you need in the field and back at your workstation. You can have one long list with subsections or multiple lists.
Investigative Process Describe step-by-step what you found and where. In an actual investigation, it is essential that you specifically describe each action taken during your investigation examination. Provide screenshots of your work for this course to demonstrate your mastery of the course lab competencies. Refer to your screenshots using sequentially numbered figures by section so figures in section five would go Figure 5-1, Figure 5-2, etc.
Summarize and explain what you have learned and why this information is essential at each step. Express in your own words what you have learned about developing and implementing a digital forensics investigation plan after you have read your reference sources. Use APA in-text citations. Include all cited sources in the reference section at the end of this plan. You should already know to stay away from Course Hero!
Do not copy and paste information from your sources. Summarize what you have learned. You can include short quotations from a reference source that helps you make your point, but it should be a phrase or two to three sentences. However, you must appropriately credit and cite the reference source. Describing your supporting analysis in your own words and quoting credible sources will help make your Project 1 paper stand out.
Interview Forms with Questions Develop separate sets of investigative questions that you would separately ask of each potential type of witness in the project. (e.g., for a company IT director, for coworkers, for witnesses). The more detailed, the better. You can learn about the types of questions to ask by reading the course references and performing your research concerning the questioning of witnesses during a digital forensic investigation. (See NIST’s Guide to Integrating Forensic Techniques into Incident Response, Special Publication 800-86; the National Institute of Justice’s (NIJ) Forensic Examination of Digital Evidence: A Guide for Law Enforcement; US Secret Service’s Best Practices for Seizing Electronic Evidence, UMGC course references, and other sources. You will also have to conduct your research to understand what to ask. Your instructor may provide some feedback on this issue.
Fully develop a list of contact people who will be essential and valuable throughout the investigation. (e.g., company, legal counsel, case investigator, case prosecutor, company IT manager, department director, employee supervisor, local law enforcement, human resources director, assigned digital forensics examiner, etc. This is a start. More contact categories may apply. Again, you will learn more about whom to contact by conducting proper research as you attempt to meet the Project 1 requirement. Don’t just make things up. Your instructor may provide some feedback on this issue.
- Investigation Timeline Create a visual timeline graphic using functions in Microsoft Word or any other familiar tool. Your graphics should be referenced and described in your report narrative (e.g. …see the interview phase in Figure 7-1. Investigation Plan Timeline). Illustrate the activities that will occur during each interval. For example, your timeline should include 30 days to image all drives, 60 days for evidence review and analysis, and 90 days for report writing and witness preparation. These time frames are just general examples of how explicitly detailed your timeline graphic and narrative work should be.
- Investigative Budget Your budget should be presented in tables using Microsoft Word, Microsoft Excel, or Mac Numbers format. Label each table with a number and title (e.g., Table 8-1: Equipment Budget, Table 8-2: Labor) for accessible referencing. Tables should contain projected/estimated costs for each line item, expenses, equipment expenses, labour expense, number of examiners, hourly rate, total estimated/projected time per examiner, number and type of computers and costs, software licensing expense, estimated imaging time per drive or electronic media, report writing time, witness preparation time, expert witness testimony time, burdensome drive expense and peripherals, and a total for all expenses. You can understand what to include by reading the resources associated with the Project 1 reference links in the course. Other examples can be obtained by checking NIST references.
- Conclusions A summary of your findings. There should be no new information here— just a condensed version of the preceding sections. It should state what you achieved. Be sure it aligns with the first section, “Purpose.”
- References Do your work supported by the sources provided in the classroom and your research? All in-text citations in other sections should be recorded in this section using APA reference page style.
- Appendices This section should include lettered appendices (Appendix A, Appendix B, and so on) if you choose to include them. In general, an appendix is where an author places supporting details that not all readers need to see, but experts or interested parties may wish to see.
Steps and instructions
A digital forensic investigation process can involve many steps and procedures. The objective is to obtain unbiased information in a verifiable manner using accepted forensic practices. In this project, you will perform some of the steps necessary for setting up an investigation. These steps include designing interview questions that establish the needs of the case and provide a focus for your investigative efforts. You will also determine what resources may be needed to conduct the investigation. Once you have this information, you can develop an investigation plan that properly sequences activities and processes, allowing you to develop time estimates and contingency plans should you encounter challenges in the investigation.
This situation involves two computers and a thumb drive. After explicit authorization to proceed has been obtained, one of the first investigative decision points is whether to process the items of evidence individually or together. Processing computers individually makes sense when they are not likely tied to the same case. However, if the computers are linked to the same case, there can be advantages in processing them together.
There are four steps in this project. In Step 1, you will develop interview protocols and identify documentation needs for a forensic investigation. In Step 2, you will identify the tools and software needed for the investigation. In Step 3, you will develop a plan for conducting the investigation, and in Step 4, you will consolidate your efforts in the form of a single document to be submitted to your supervisor (i.e., your instructor). The final assignment in this project is a planning document with a title page, table of contents, and a distinct section for each of the three steps in the project. Consult the relevant Guidelines for Project 1 Investigation Project Plan sections at every step.
In Step 1, get started on the plan by creating an interview form to record questions, keywords, and authorization information and to complete the legal forms needed in this case. However, before you can do that, you need to review your training in criminal investigations.
Step 1: Create and Gather Forms
Your tasks in Step 1 are to create interview forms to record questions, keywords, and authorization information and designate other legal forms needed in this case. You must describe the importance of each form you create in the body of your final Project Plan assignment and include in-text reference citations for all of your content. The forms you complete as part of Step 1 will be included in your Investigation Project Plan, the final assignment for this project.
As part of the investigation into two computers and a thumb drive, it’s essential to do the necessary preliminary work. Criminal investigations have laws governing the chain of custody, search warrants, subpoenas, jurisdiction, and the plain view doctrine. It’s essential to be familiar with these topics. Review forensic laws and regulations related to cybercrime, as well as rules of digital forensics, in preparation for your digital forensic investigation.
The next thing to do is to read the police report and perform a quick inventory of devices that are thought to contain evidence of the crime. You have set up a meeting with the lead detectives and the prosecutor handling the case.
You have received an official request for assistance that gives you the authority to conduct the investigation. You realize it will be impossible to produce a detailed investigation project plan before you meet with the detectives and the prosecutor. First, you must develop questions to establish the key people and activities. These questions should address potential criminal activity, timelines, and people who must be investigated.
It is also essential to determine whether other investigators are pursuing different aspects of the case and to include those investigators on your contact list. In addition, some situations may involve organizations or individuals who must adhere to various industry compliance types. This situation may require you to follow special procedures.
In Step 2, you will consider the resources needed for the investigation.
Step 2: List Required Forensic Equipment, Software, and Labor Expenses
In Step 1, you developed forms and templates to collect the legal, criminal, and technical information that lays the groundwork for your investigation. In this step, you will consider the types of equipment and human resources needed to conduct the investigation and create a budget table that includes expenses for software licenses, computers, storage devices, number of digital forensics examiners, digital forensics examiners’ labour hours, examiner hourly pay rate, including time spent for each phase of the investigation process in gathering evidence analysis, reporting, presentation preparation and court appearance(s).
It is essential to total the overall costs of all equipment and expenses in your budget table. By making these preparations, you are establishing forensic readiness. Required resources can include people; tools and technologies such as RAID storage, deployment kits, or imaging programs; and budget and timeline information.
Develop a checklist. It will be included in the final Investigation Project Plan.
In the next step, you will begin to prepare a plan for managing a digital forensic investigation.
Step 3: Plan Your Investigation
In the prior step, you determined the necessary resources for your investigation. In this step, you will develop a plan for managing the investigation. The requirements for writing case reports reflect the step-by-step rigidity of the criminal investigation process itself. Articulating time, task, money, and personnel requirements is essential.
Project management is a skill set that is not often linked to digital forensics and criminal investigations. That is unfortunate because effective project management can dramatically impact the success and accuracy of an investigation. Identifying the tasks that need to be performed, their sequence, and their duration are essential considerations, especially in the face of “wild cards”, such as delays in obtaining correct search warrants and subpoenas. It is also essential to clearly understand the goals for the investigation, as you will likely be called upon to present conclusions and opinions of your findings.
Your project plan should include a properly sequenced narrative timeline and a separately labelled and sequenced Visual Graphic Timeline chart that reflects the time intervals between each phase of the evidence acquisition and investigation processes (e.g., 30 hours gathering evidence spread across five business days, 60 hours of analysis over ten business days, 90 days for reporting and court preparation, etc.) including detailed time estimates, and contingency plans. Your plan will serve many purposes, including assigning a project budget. As you create your plan, be sure to include in your meeting agenda communications and reporting: who should be involved, how the activities should be carried out, how often, and under what circumstances (i.e., modality, frequency).
Once you have developed your project management plan, move on to the next step, where you will submit your final assignment.
Step 4: Prepare and Submit the Completed Investigation Project Plan
For your final assignment, you will combine the results of the previous three steps into a single planning document—an Investigation Project Plan—with a title page, a table of contents, and a distinct section for each step. The plan should include:
- Forms documenting key people, meeting agenda, key activities and reporting, keywords, investigation timeline narrative, visual graphic timeline chart, authorization confirmation (e.g., ownership, jurisdiction), and related investigations. Designation of the legal forms required for criminal investigations should also be included. (Step 1)
- Resource checklist for equipment, human resources and labour expenses (Step 2)
- Management plan (Step 3)
- Search and seizure form(s)
- Chain of custody form
The organization and details of your plan are essential. Be sure to refer to the Guidelines for Project 1 Investigation Project Plan to meet the minimum standards needed for this project.
All sources of information must be appropriately referenced. Submit your completed Investigation Project Plan to your supervisor (instructor) for evaluation upon completion.
Check Your Evaluation Criteria
Before you submit your assignment, review the competencies below, which your instructor will use to evaluate your work. A good practice would be to use each competency as a self-check to confirm you have incorporated all of them. To view the complete grading rubric, click My Tools, select Assignments from the drop-down menu, and then click the project title.
- 1.1: Organize the document or presentation clearly that promotes understanding and meets the assignment’s requirements.
- 2.2: Locate and access sufficient information to investigate the issue or problem.
- 4.1: Lead and participate in a diverse group to accomplish projects and assignments.
- 5.1: Demonstrate best practices in organizing a digital forensic investigation.
- 5.2: Utilize Project Management principles in an investigation.